Server
来源:百度文库 编辑:神马文学网 时间:2024/05/23 13:36:27
R/Evolution Storage Architecture

Dot Hill has pioneered a revolutionary new storage architecture for the Volume Storage Market: the Rapid Evolution Storage Architecture™. This highly modular, highly dynamic system is designed to rapidly evolve and support OEM technology, enabling OEMs to quickly achieve sustainable competitive advantage in the Volume Storage Market.
The Rapid Evolution Storage Architecture, or R/Evolution™ Architecture, delivers the high levels of performance, storage density, time-to-market leadership and - most importantly - configuration flexibility required in the Volume Storage Market. Using modular and bladed components, the R/Evolution Architecture provides OEMs with a "Configure-to-Product" model (not just "configure-to-order") that lets them customize Volume Storage Market solutions quickly, easily and precisely. This unique model revolutionizes how OEMs bring storage products to market by ensuring opportunities for product differentiation, even between different companies that simultaneously OEM product from Dot Hill. Important benefits of the R/Evolution Architecture include: Significantly faster time-to-market that allows OEMs to quickly roll out highly targeted Volume Storage Market solutions and preempt their competition. Lower OEM costs at every stage of new product introduction. These substantial development and introduction savings help enable market leading pricing for Volume Storage Markets and enhance OEM profitability. Faster, easier integration of OEM value-added technologies or capabilities, providing greater opportunities for differentiation in the Volume Storage Market.
Key Macro Trends Impacting the Volume Storage Market
The Volume Storage Market is under intense pressure. New regulatory requirements and evolving business demands are driving the need for Volume Storage Market solutions that hold down costs, yet deliver more and more enterprise-level features, capabilities and software. Why? Data from applications like file serving, disk-to-disk backup, short-term archiving and near-line storage of bulk data must be quickly and readily available to multiple users. Yet because this data is not always mission-critical, it is uneconomic to store it on high-availability, mission-critical storage systems with prohibitive per-GB-costs. In addition, regulations like Sarbanes-Oxley and HIPAA mandate the ability to rapidly access enormous quantities of financial and medical data. Although this data may be months or years old, nonetheless, tape archive is not a viable solution due to the extensive time required to restore from tape. Thus, tiered storage strategies—which seek to properly balance costs and capabilities in order to efficiently store this rapidly expanding pool of "in-between" data—are becoming critical in the Volume Storage Market.Below are key macro trends that are driving the Volume Storage Market: Tiered Storage - In the broad and highly diverse Volume Storage Market, one size does not fit all. Organizations need storage solutions that mix and match performance, availability, cost and capabilities to address the specific needs of each storage tier in the organization. In addition, new technologies and the application of existing/repackaged technologies, such as ILM (Information Lifecycle Management), D2D (Disk-To-Disk) backup, CAS (Content Addressable Storage), and CDP (Continuous Data Protection) are requiring greater flexibility and intelligence in every dimension of the storage solution…not just at the time of purchase, but over the lifetime of the storage solution. Thus, the increasing need for tiered storage that can evolve and adapt, efficiently and gracefully. Regulatory - New regulations such as SEC 17a-4, SarBox section 404 and HIPAA are driving new mission-critical, tiered storage strategies in every organization. Data such as financial information, medical records, and email correspondence must not only be tracked, protected and secured, but also must be globally available upon demand. Given the dynamic nature of these requirements, storage solutions with architectures that embrace modularity, "pay-as-you-go" economics and easy scalability/upgradeability throughout the product lifecycle are likely to work best for IT customers. Security - The ability to ensure trusted access to data is one of the factors driving enhanced intelligence, access control and authentication capabilities in the storage market. As in the networking and telecommunications industries, the ability to enhance security while still providing productive access for authorized users is vital for business success. Blades and Grids - The growth of blade servers and grid computing is driving new SAN (Storage Area Network) configurations and interface requirements. As the networks for communication, networking, cluster computing and storage move closer together, flexible, intelligent and "grid-aware" storage platforms are required. Storage platforms must be ready for this unified networking environment and provide a graceful path to moving/migrating between or across these varied networking requirements. More than hardware, this must include intelligent data and virtualization software services to deal with the myriad of combinations and configurations. Business Continuance - Ensuring that operations continue without disruption is a leading priority for IT organizations worldwide. This requirement has lead to an increased use of disk-based solutions for replication of data in remote sites for business continuance, using disk-to-disk (versus tape) for backup to make recovery instantaneous and using tiered disk-storage strategies for cost-effectively archiving data online in order to meet regulatory requirements. Object-Based Storage - Object-Based Storage (OBS) is vital to the next generation of file systems such as Microsoft‘s WinFS. OBS will require a new approach to storage access, security, intelligence and management. Without a solid, well conceived architecture, current storage solutions could have difficulty migrating to OBS technology. Thus, it‘s essential that Volume Market storage solutions have designs that can easily accommodate the new layers of capability and intelligence that manage not only the primary data, but the meta-data that will be vital to the next generation of optimized data access, search and retrieval. Disk Storage Growth - Disk storage is growing in three principal ways. First, the number of files generated by computers continues to grow at an accelerated rate. Second, customers are using formats that generate larger file sizes, so the same number of files takes up more disk space. Finally, files that previously were stored on tape are now being stored on disk for data protection and for regulatory purposes (due to access time requirements). These factors require not only more storage, but storage that is optimized (cost and performance) for each application.
Volume Market Storage Requirements
Five years ago, the storage market was much simpler. The very high end of the mainframe and mission-critical markets demanded the highest performance and availability. The Volume Storage Market supported work groups and non-mission critical applications, and the entry-level market was a collection of small/standalone systems that were very low cost, and not very functional.
Today the storage industry is much different. Although the volume of data continues to grow exponentially, enterprises are no longer willing to endlessly invest in high-end storage systems. Further, there is an ever-increasing volume of data that falls "in-between" these high-end, online storage systems (with their high cost-per-GB), and low-cost, high-capacity tape archival systems (with their slow, labor-intensive data retrievals). What‘s more, the availability, access, protection, security and performance requirements for this "in-between" data can vary greatly, depending on its particular use: Databases and e-commerce that require high performance, I/O-intensive application computing High-capacity, cost-effective storage to meet regulatory requirements Near-line archive of infrequently used data that nonetheless must be available at all times Cost-effective storage of data generated by email and office productivity applications
For IT managers, tiered storage offers a solution to this dilemma. Yet tiered storage solutions must do more than merely provide high capacity, optimal performance, low cost-per-GB and easy integration into established enterprise infrastructures. They must also be able to adapt and evolve rapidly so that they can deliver the optimal balance of cost/performance levels for every type of data. In short, the Volume Storage Market can be characterized by its overarching requirement for configuration flexibility. This requirement has made the Volume Storage Market the most challenging and exciting segment in the storage business. It also demands a much more modular and flexible architecture, one that can be quickly and cost effectively optimized to balance the various metrics that define storage solutions: Performance - IOPS (Inputs/Outputs per Second) and data rates (the speed at which the data is transferred during IOPS) are the two fundamental measurements of performance. These benchmark numbers are the basis for defining storage performance in the market. The ability to provide and optimize IOPS and data rates for key applications is vital to providing the right solution for each application. Manageability - The ability to control, configure, allocate and deploy storage resources is perhaps the greatest factor in the ultimate cost—and value—of a storage solution. Reducing human interactions and increasing automated/proactive operations are two key factors impacting overall efficiency and lowering total cost-of-ownership. Protection - New regulations and competitive requirements make the cost of data protection one of the key decision points in selecting any storage solution. Every level of the storage solution should offer various levels of data protection to meet the specific needs of each class of data. Cost - The market is segmented based on the cost to achieve desired levels of performance, manageability, protection, and density/capacity. Acquisition cost is most visible, but cost of ongoing operations/management has the greatest effect on total cost of ownership. Density/Capacity - Measurement of the number of disks that can fit into a standard unit of rack space. By maximizing density and capacity, IT departments can get more total IOPS and greater overall data throughput rates per individual rack. Storage Tiers - While one size does not fit all, one integrated storage strategy is vital to getting maximum value out of capital dollars invested. Tiered Storage provides the ability to integrate various storage personalities under a single architecture.
While the first five metrics apply to all segments of the storage market, the final metric—Storage Tiers—is unique to the Volume Storage Market. It is the critical factor for delivering the most cost effective solutions, optimized across a broad range of features, functionalities and capabilities. For OEMs, success in this arena lies in the ability to capitalize on a storage architecture that is modular and flexible enough to meet all of these widely varying demands—both when the solution is purchased and over the life of the solution. At the same time, the architecture must share core technologies so that it is completely interoperable across different configuration and iterations.
This is why Dot Hill has pioneered the Rapid Evolution Storage Architecture. It is a single, integrated storage platform that can deliver maximum configuration flexibility in Volume Market storage solutions. Its extreme modularity and "Configure-to-Product" model provide the ability to rapidly create solutions that can be selected by each OEM to meet the specific needs of their targeted markets and the positions they wish to claim. The Rapid Evolution Storage Architecture, or R/Evolution Architecture, not only allows OEMs to balance the features and capabilities so critical to success, it also provides the tools to optimize for only one of the metrics, or all six metrics of the Volume Storage Market.

Rapid Evolution Storage Architecture
OEMs require a Volume Market storage platform that gives them market flexibility and product adaptability so they can deliver storage solutions that successfully address the market factors previously outlined. Further, their solutions must offer their customers investment protection, with the ability to easily and cost effectively adapt as new demands and/or requirements are placed upon their storage strategies. The R/Evolution Architecture does this, providing: Core technologies shared across chassis platforms Highly modular, blade-driven architecture Easy integration of OEM value-add/storage applications Advanced file and storage management services Common spares and field upgrades
These foundational attributes of the R/Evolution Architecture are further enhanced by Dot Hill‘s corporate culture of responsiveness and flexibility. As a partner, Dot Hill has a proven track record of supporting innovative business models in order to meet the needs of its OEM customers, as well as their end-user customers. The net result: the benefits of off-the-shelf pricing and flexibility, combined with the ability to radically customize the features and functions of storage solutions... during development and after deployment.

The R/Evolution Architecture provides a roadmap for the future of the many market factors driving storage today. Its common technology core supports a dynamic path to expanding performance, capabilities, capacity and manageability, protecting against obsolescence and allowing OEMs and their customers to easily and affordably meet evolving storage needs over the lifetimes of their storage systems. This provides a higher level of investment protection, without the overhead inherent in solutions that don‘t use the R/Evolution Architecture. In sum, the products that OEMs build will now be as dynamic as the markets they work in…today and tomorrow.
Tiered Storage Modules (TSM)
The R/Evolution Architecture Tiered Storage Modules support RAID, SBOD (Switched BOD) and JBOD configurations that deliver some of the industry‘s highest levels of drive density and the most efficient use of standard rack space. The R/Evolution Architecture supports multiple chassis configurations and can support Fibre Channel (FC), Serial-Attached SCSI (SAS) and Serial ATA (SATA) drives, all in a single system…all in the same rack. This flexibility allows OEMs to precisely balance the metrics of cost, protection and performance in their Volume Storage Market solutions.
The R/Evolution Architecture provides 20% more disk drives in a typical rack. This means greater capacity, better performance and greater cost effectiveness, which translates into higher data rates/IOPS-per-rack in the data center.

Host Iinteface Modules (HIMS)
HIMs are one of the components of the PDC module. A HIM allows the controller connection to the host to be changed between interfaces. Initially, R/Evolution Architecture will support 4Gb FC, 3Gb SAS and 1GbE iSCSI connectivity. In addition, the HIM offers the ability to easily add new interfaces such as 10Gb iSCSI, 8Gb FC, Infiniband and other host interconnections. This allows OEMs and their customers to readily anticipate and adapt to the convergence of storage interfaces.

Performance Data Controllers (PDCS)
The core controller technology of R/Evolution Architecture provides performance where and when it is needed. The flexible design is capable of moving data at up 1.5GB/s and at over 200K IOPS, delivering up to twice the performance of competitive Volume Storage Market solutions. With multiple performance and protection parameters available, the PDCs provide a modular approach that allow OEMs to finely balance cost and performance metrics. They also provide post-deployment adaptability for end user customers. The PDC supports multiple CPU speeds and cache increments from 512MB to 2GB per controller. The PDC is comprised of three components: the RAID I/O module, the Host Interface Module (HIM) and the Drive Module (DM). The RAID I/O module is the RAID engine for the R/Evolution Architecture. Not only is it a highly flexible software core for RAID capabilities, the RAID I/0 also hosts the Dot Hill Storage Services software and includes the management engine for the R/Evolution Architecture. Dot Hill‘s unique PowerFlex RAID technology and our patent-pending SimulCache provide industry-leading write performance. In addition, PowerFlex RAID allows the flexibility to run either Dot Hill or OEM RAID cores to improve OEM integration. (The HIMs and DMs are discussed in other sections.)

Drive Modules (DMS)
DMs are one of the components of the PDC module. A DM provides the flexible option for adding, changing or expanding new drive interfaces in a single architecture.

Storage Application Blades (SABS)
The high speed back plane of the R/Evolution Architecture supports multiple types of blades, including server blades, cluster fabric blades, and other OEM application hardware blades. Using industry standard interfaces, SABs of the R/Evolution Architecture can adapt to the needs of the environment, providing differentiation opportunities as well as investment protection. OEMs can use these blades to host value-added software and build solutions that target multiple verticals and/or enterprise applications…all on the same core platform. In this era of commoditization and shrinking margins, SABs may provide the best opportunity for solution differentiation and greater profitability.
Dot Hill Storage Services (DSS)
Snapshots - Snapshots provide the ability to create a Point-In-Time copy of a disk volume. Dot Hill Storage Services can create full snapshots of volumes or delta snaps of recent changes. It provides customers the ability to roll-back to any point in time. These disk images can be used to replicate data, create a new working volume or as a business continuance volume Remote Replication - One of the keys to ensuring business continuance is the ability to protect data over distances in case of local/regional events such as fire, hurricane or earthquake. Dot Hill Storage Services provides the ability to replicate and protect data over any IP network to anywhere across the globe. Remote volumes can be read, read-write and boot volumes if the OS permits remote boot devices RAIDar Manager - Dot Hill‘s RAIDar Manager provides the ability to create, configure and control disk volumes dynamically without interrupting operations. It provides users with complete control and reporting tools over every aspect of their storage system Storage Presentation Services - Dot Hill‘s storage presentation services provide the ability to present storage in a variety of ways. It enables file services, storage virtualization, resource management, cross-vendor APIs, flexible software and feature licensing, as well as support for industry standards such as SMI-S. These services enable OEMs to build solutions that are tightly integrated into existing product lines and create unique value-add.

The R/Evolution Architecture Advantage
At the heart of the R/Evolution Architecture is our highly modular, blade-driven design. This "modular core" provides a comprehensive range of configuration options to OEMs, as shown in the diagram below. Each module component allows OEMs to craft a personality and target application for their solutions, all with a low-cost, build-to-order model. In addition, this highly modular, blade-driven design provides easy, future upgradeability for OEM end-user customers, ensuring investment protection and long-term ROI.
The ability to select specific module components and options within the R/Evolution Architecture makes possible virtual "off-the-shelf" solutions that target various sub-segments of the Volume Storage Market. In addition, it allows OEMs to create highly differentiated solutions within their own niche segments. The diagrams shown here and the chart further down demonstrate how various configurations can be quickly identified, illustrating that even though one size does not fit all in the Volume Storage Market, one architecture can…and does.

Finally, the R/Evolution Architecture not only meets the needs of the Volume Storage Market today, it provides a compelling roadmap to the future. As the storage market continues to evolve on a daily basis, most changes will be small and incremental. Yet even if they are sudden and dramatic, the bladed, modular, interchangeable nature of the R/Evolution Architecture will allow OEMs and their customers to rapidly and painlessly adapt to these changes. One of the best examples is the change in storage networking performance. While a major jump in performance may send some market players into a frenzy of "market-tecure" or "slide-ware" in order to define how they will cope with the new changes, the R/Evolution Architecture provides OEMs with a simple solution that will allow them to effectively manage these changes in advance.

Business Advantage For OEMs: R/Evolution Architecture + Dot Hill
Dot Hill provides a revolution in how OEM‘s bring storage products to market. The R/Evolution Architecture helps OEMs accelerate their time-to-market and reduce development costs, while providing an integrated storage platform that makes it easier to incorporate value-added offerings that enhance differentiation and increase profitability.
Time-to-Market Advantage
The R/Evolution Architecture creates a single design core that can be used across multiple families of products. The products can bridge different chassis sizes, host connections, drive types and price points. It provides a common parts and service capability across those product families. In short, the R/Evolution Architecture enables OEMs to capitalize on a "Configure-to-Product" model to dramatically reduce time to market.
Development Savings
The R/Evolution Architecture lowers the cost of new product introduction at every stage for OEMs—from concept to design to manufacturing. This enables substantial development savings for OEMs, delivers market leading pricing for Volume Storage Markets and enhances OEM profitability. But the advantages are not just about products. They extend to Dot Hill‘s flexible business model and ability to support any level of joint development and go-to-market model on a global basis. This allows OEMs to focus on the part of the program/product that creates the maximum value for OEMs and their customers.
Storage Integration Platform
The R/Evolution Architecture provides a host platform for OEM value-add applications. As software value-add continues to define differentiation in the market, Dot Hill is committed to providing the ideal Volume Market storage platform to enable these profitable solutions. The combination of Dot Hill‘s core Storage Services software and OEM value-add applications can create a powerful force in the market.
Summary
As the Volume Storage Market continues to evolve, Dot Hill and its R/Evolution Architecture will continue to meet the needs of OEMs and their customers. The ever-increasing need for modularity, flexibility, performance and enterprise data management features will only grow. The R/Evolution Architecture is the integrated platform that provides a complete, flexible template for OEMs to build winning solutions for every segment of the Volume Storage Market, and for their customers to have access to simple, cost-effective upgrades in the future, protecting their investments.
Download PDF Version (4.5MB PDF)
R/Evolution Demo (8MB Zip)
Why Dot Hill? (472KB PDF)
The 2730 Data Sheet (504KB PDF)
http://www.dothill.com/
The Linley Wire
Independent Analysis of the Networking-Silicon Industry
Volume 5, Issue 8
April 20, 2005
Editor: Linley Gwennap
Contributors: Bob Wheeler, Jag Bolaria, Sanjay Iyer
In This Issue
NPU Market Sees Broad-Based ExpansionAlacritech Blocks Microsoft ChimneyAdaptec Exits Chip BusinessIDT Unveils Interconnect StrategyNews In BriefSeminar Program Updates
A Guide to Storage Networking Silicon is now available for immediate delivery. Get up-to-date information on storage networking, including SAN, NAS, and IP storage. New in this edition is coverage of Fibre Channel and SAS/SATA devices, an emerging category of storage processors that is starting to heat up. For more information, visit ourweb site.
NPU Market Sees Broad-Based Expansion
The Linley Group has completed its survey of the network-processor market for 2004. Our final data shows NPU revenue grew an outstanding 61% over 2003 to reach $145 million. The market even managed to grow slightly in 2H04 over 1H04, despite market-leaders AMCC and Intel suffering revenue declines. The inventory correction seen across the broader markets slowed, but did not stall, NPU expansion.
Our data also reveals that, with only one exception, every vendor increased its NPU revenue in 2004. Intel contributed the most dollars to the market’s growth, gaining 6% market share as a result. Despite losing an equal amount of share, AMCC still increased its NPU revenue by more than any vendor except Intel. Thanks to initial shipments of its APP500 family, Agere gained share while nearly tripling its NPU revenue.

Hifn increased revenue from the former IBM PowerNP line by about 40%, resulting in a small share loss. But with first-year revenue surpassing the amount Hifn paid for the product line, the company should be very pleased with its results. Vitesse continues to defy gravity, maintaining share without active product development. Although Vitesse clearly has the most profitable NPU business of any vendor, it will begin losing share as current design wins reach end of life. As the only vendor to experience declining NPU revenue in 2004, Freescale is already seeing its discontinued C-Port line ramp down.
Startups Wintegra and EZchip showed strong growth, thanks to their focus on the underserved access and 10Gbps markets, respectively. Wintegra was the leading NPU startup in 2004, roughly doubling its revenue over 2003. EZchip nearly tripled its revenue in 2004, but its share of the overall market remained below 5% in 2H04.
Although 2004 closed stronger than anticipated, we continue to believe that NPU growth will slow this year. We now expect the NPU market to reach about $175 million in 2005. This slower growth rate should be sustainable through 2008, however, as NPUs continue to replace ASICs and fixed-function ASSPs. —BW
Complete coverage of the NPU market appears in our reportA Guide to Network Processors.
Alacritech Blocks Microsoft Chimney
The Vatican may be blowing smoke, but Microsoft’s TCP Chimney isn’t, after U.S. District Court judge Jeffrey White granted Alacritech a preliminary injunction preventing Microsoft from developing or distributing its TCP offload software. A pioneer in the development of TCP offload, Alacritech had sued Microsoft for infringing on its patent 6,697,868, one of several patents that Alacritech has been granted on its technology.
Several companies have developed TCP offload chips, ranging from giants such as Broadcom to startups such as Astute and Silverback. TCP offload is useful for Gigabit Ethernet connections, reducing the load on the main server processor, and highly recommended for 10 Gigabit Ethernet. Most of these chips don’t work with Microsoft Windows today but will work with TCP Chimney, due to be released in mid-2005 as part of the Scalable Networking Pack for Windows Server 2003 and also as part of the “Longhorn” operating system in 2006.
Alacritech’s legal action may stall these releases or cause Microsoft to remove TCP Chimney from the code. Microsoft has already been forced to strip TCP Chimney from its beta releases and is forbidden from doing internal testing or development. If this situation continues for months or years, it would severely limit the revenue potential of the chip companies in this space and slow the adoption of 10G Ethernet.
Microsoft has few options. It can appeal the injunction, but such appeals are rarely won. It can hope to prevail in a full trial, but the 868 patent clearly bears on TCP Chimney, and Judge White has already rejected Microsoft’s claims that the patent is invalidated by several cases of prior art. Unless Microsoft comes up with additional instances of prior art, its chances of winning at trial are poor. Even if it does eventually prevail, its TCP offload plans could be in limbo for several months, pushing TCP Chimney out of the Longhorn release and beyond the window for 10G Ethernet deployment.
We expect Microsoft to instead settle the case. Because Alacritech disclosed its TCP technology to Microsoft in 1999 under a non-disclosure agreement, Microsoft could be found liable of “willful violation.” Such a finding would result in triple damages, an amount that could easily exceed $100 million. The software giant would be better off cutting a big check to Alacritech instead of stalling the adoption of TCP offload technology. —LG
Additional coverage of TCP Chimney and TCP offload chips appears in our recent reportA Guide to Gigabit and 10G Ethernet Silicon.
Adaptec Exits Chip Business
Last week, Adaptec and Vitesse took the wraps off an alliance that positions Vitesse as a preferred SAS silicon supplier to Adaptec. The first products from this alliance—the single-chip VSC7250 and VSC7251 RAID controllers—combine Adaptec’s software and RAID 5/6 hardware accelerators with Vitesse’s CPU and SAS PHY technology to deliver up to 4GB/s RAID throughput. The VSC7250, which provides 8 SAS ports and uses an eight-lane PCI Express interface, lists for $64 in high volumes; the VSC7251, with four SAS ports and a four-lane PCI Express interface, lists at an affordable $46. These low-priced RAID controllers address a potentially huge SOHO and SMB market. Both devices will sample in May.
In a separate development, Adaptec struck a deal to outsource development of a 10Gbps iSCSI controller to startup ServerEngines, instead of using the in-house team from its Platys acquisition. The 10Gbps controller will be compatible with Adaptec’s current Vega controllers. Like the Vitesse deal, the ServerEngines agreement includes the transfer of some Adaptec engineers and intellectual property to jump-start development.
Taken together, these two deals signal the end of chip development at Adaptec. Perhaps not coincidentally, Ahmet Houssein recently left his role as GM of Adaptec’s Storage Solutions group, which developed SAS and iSCSI chips, to become CEO of storage-processor startup Silverback. Adaptec’s move acknowledges that storage silicon is on its way to becoming a commodity, moving the value to software, interoperability, and support. While semiconductor vendors such as AMCC and LSI juggle a storage-systems business alongside their primary semiconductor business, Adaptec has wisely chosen to drop silicon development and focus only on systems and software; its new priorities mean that the company can expand its storage-systems business, as it did by acquiring SAN-server vendor Snap Appliance. Adaptec’s chipless strategy is a boon to Vitesse and ServerWorks, who gain a special relationship with a seasoned storage vendor. —SI
Complete coverage of storage processors appears in our reportA Guide to Storage Networking Silicon.
IDT Unveils Interconnect Strategy
This week, IDT announced plans to offer a family of RapidIO switches, which it expects to sample in early 2006. These switches will be useful in connecting clusters of DSP and embedded processors in wireless infrastructure and similar applications. Previously, IDT had announced SPI-4 bridges and PCI Express bridges and switches, as well as its plans to offer components for ASI. The combination of these products represents a concerted effort to address board-level and system-level interconnect beyond the PC.
IDT has focused on developing several board-level interconnects for specific market segments but a common system-level interconnect. The company has not announced plans to offer system-to-system interconnect products, however. IDT appears to have segmented board-level requirements among networking, wireless infrastructure, and embedded applications. The common board-level interconnect technologies used in these applications are SPI-4, RapidIO, and PCI Express/RapidIO, respectively. IDT plans to offer a bridge and switch product for each of these technologies. The boards using these technologies are then connected over the system backplane using ASI. The company has yet to announce details on its ASI products.
IDT is embarking on a clear strategy, which offers it the potential to establish leadership in the rapidly growing interconnect market. A critical factor for this strategy, however, is the timing for the adoption of new technologies such as RapidIO and ASI. Additionally, the company must execute on several development fronts before it can translate the strategy into real revenue. —JB
Complete coverage of IDT’s newest products and other interconnect products will occur at our live seminar event on April 27 (see below).
News In Brief
Xelerated has closed a $17 million third round of funding. This round included new investors Accel Partners and Amadeus Capital Partners. Xelerated says the new funding should carry the company to profitability, which is expected in 2006. Separately, Xelerated says it has taped out its X11 second-generation network processor and that early samples will reach customers in July. Considering that Xelerated originally targeted the OC-768 market, the startup deserves a great deal of credit for surviving the NPU market consolidation. —BW
Complete coverage of Xelerated appears in our reportA Guide to Network Processors.
Earlier this month, TeraChip announced that it had raised an additional $7 million from Accel Partners and Benchmark Capital. The company has also added a new CEO, Rod Kay, replacing Micha Zeiger, who takes over as the Chairman of the board and CTO. Now, the startup needs a new direction and flawless execution to establish a market position. With the latest funding, TeraChip will need to leverage its existing architecture to create a new family of fabric products that is differentiated from existing products and targets a developing market: a tall order for a startup that has yet to make its mark. —JB
Seminar Program Updates
Join us on April 27 in San Jose, CA for a free one-day seminar on Fabrics and High-Speed Interconnects. This technical program will consist of a tutorial by Jag Bolaria, senior analyst at The Linley Group, followed by three in-depth sessions packed with information from industry leaders.
New additions to the technical program:
* Ron Wilson, Semiconductor Editor, EE Times, "EE Times Backplane Survey Results"
Session I: Board Level Interconnects:
* Delfin Rodillas, Staff System Architect, Xilinx, "FPGA Serial Interconnects"
* Brad Booth, Chair, IEEE P802.3an Task Force, will join the panel discussion
Session II: Panel Discussion: Selecting the Future Form Factor
This panel will include the leading proponents of the various form factors available in the industry, including ATCA, SIOM, VME, and more.
Panelists include: Eddie Reid, Chair, PCI-SIG PCI Express, SIOM; Rob Davidson, VP of Marketing, ATCA; Melissa Heckman, Vice Chair of the VSO, VME; Andrew Alleman, Systems Architect, Radisys
Session III: System or Advanced Interconnects
* David Formisano, Technical Marketing Manager, Intel, "Connecting the Modular Communications Platform: Standard Fabrics and Interconnects"
* Ed Bollet, Product Director, InfiniBand, will join the panel discussion
For the full program of topics and speakers, visit ourweb site.
The seminar is free to qualified individuals who register early. Non-qualified registrants will be charged a fee. For complete details and registration information, visit theseminar page.
This event is sponsored by IDT, StarGen, Sandburst, Intel, Xilinx, and InfiniBand Trade Association.
To receive The Linley Wire via e-mail,click here
About The Linley Wire
http://www.linleygroup.com/Reports/storage_guide.html
全方位讲解硬件防火墙的选择(多图)
http://www.sina.com.cn 2005年01月05日 13:48 天极网
文/tanker
防火墙是指设置在不同网络(如可信任的企业内部网和不可信的公共网)或网络安全域之间的一系列部件的组合。它是不同网络或网络安全域之间信息的唯一出入口,通过监测、限制、更改跨越防火墙的数据流,尽可能地对外部屏蔽网络内部的信息、结构和运行状况,有选择地接受外部访问,对内部强化设备监管、控制对服务器与外部网络的访问,在被保护网络和外部网络之间架起一道屏障,以防止发生不可预测的、潜在的破坏性侵入。防火墙有两种,硬件防火墙和软件防火墙,他们都能起到保护作用并筛选出网络上的攻击者。在这里 主要给大家介绍一下我们在企业网络安全实际运用中所常见的硬件防火墙。
一、防火墙基础原理
1、防火墙技术
防火墙通常使用的安全控制手段主要有包过滤、状态检测、代理服务。下面,我们将介绍这些手段的工作机理及特点,并介绍一些防火墙的主流产品。
包过滤技术是一种简单、有效的安全控制技术,它通过在网络间相互连接的设备上加载允许、禁止来自某些特定的源地址、目的地址、TCP端口号等规则,对通过设备的数据包进行检查,限制数据包进出内部网络。包过滤的最大优点是对用户透明,传输性能高。但由于安全控制层次在网络层、传输层,安全控制的力度也只限于源地址、目的地址和端口号,因而只能进行较为初步的安全控制,对于恶意的拥塞攻击、内存覆盖攻击或病毒等高层次的攻击手段,则无能为力。
状态检测是比包过滤更为有效的安全控制方法。对新建的应用连接,状态检测检查预先设置的安全规则,允许符合规则的连接通过,并在内存中记录下该连接的相关信息,生成状态表。对该连接的后续数据包,只要符合状态表,就可以通过。这种方式的好处在于:由于不需要对每个数据包进行规则检查,而是一个连接的后续数据包(通常是大量的数据包)通过散列算法,直接进行状态检查,从而使得性能得到了较大提高;而且,由于状态表是动态的,因而可以有选择地、动态地开通1024号以上的端口,使得安全性得到进一步地提高。
2、防火墙工作原理
(1)包过滤防火墙
包过滤防火墙一般在路由器上实现,用以过滤用户定义的内容,如IP地址。包过滤防火墙的工作原理是:系统在网络层检查数据包,与应用层无关。这样系统就具有很好的传输性能,可扩展能力强。但是,包过滤防火墙的安全性有一定的缺陷,因为系统对应用层信息无感知,也就是说,防火墙不理解通信的内容,所以可能被黑客所攻破。

图1:包过滤防火墙工作原理图
(2)应用网关防火墙
应用网关防火墙检查所有应用层的信息包,并将检查的内容信息放入决策过程,从而提高网络的安全性。然而,应用网关防火墙是通过打破客户机/服务器模式实现的。每个客户机/服务器通信需要两个连接:一个是从客户端到防火墙,另一个是从防火墙到服务器。另外,每个代理需要一个不同的应用进程,或一个后台运行的服务程序,对每个新的应用必须添加针对此应用的服务程序,否则不能使用该服务。所以,应用网关防火墙具有可伸缩性差的缺点。(图2)
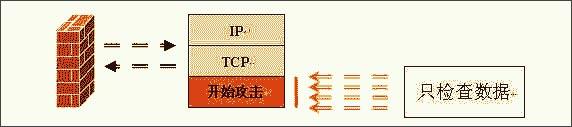
图2:应用网关防火墙工作原理图
(3)状态检测防火墙
状态检测防火墙基本保持了简单包过滤防火墙的优点,性能比较好,同时对应用是透明的,在此基础上,对于安全性有了大幅提升。这种防火墙摒弃了简单包过滤防火墙仅仅考察进出网络的数据包,不关心数据包状态的缺点,在防火墙的核心部分建立状态连接表,维护了连接,将进出网络的数据当成一个个的事件来处理。可以这样说,状态检测包过滤防火墙规范了网络层和传输层行为,而应用代理型防火墙则是规范了特定的应用协议上的行为。(图3)

图3:状态检测防火墙工作原理图
(4)复合型防火墙
复合型防火墙是指综合了状态检测与透明代理的新一代的防火墙,进一步基于ASIC架构,把防病毒、内容过滤整合到防火墙里,其中还包括VPN、IDS功能,多单元融为一体,是一种新突破。常规的防火墙并不能防止隐蔽在网络流量里的攻击,在网络界面对应用层扫描,把防病毒、内容过滤与防火墙结合起来,这体现了网络与信息安全的新思路。它在网络边界实施OSI第七层的内容扫描,实现了实时在网络边缘布署病毒防护、内容过滤等应用层服务措施。(图4)

图4:复合型防火墙工作原理图
3、四类防火墙的对比
包过滤防火墙:包过滤防火墙不检查数据区,包过滤防火墙不建立连接状态表,前后报文无关,应用层控制很弱。
应用网关防火墙:不检查IP、TCP报头,不建立连接状态表,网络层保护比较弱。
状态检测防火墙:不检查数据区,建立连接状态表,前后报文相关,应用层控制很弱。
复合型防火墙:可以检查整个数据包内容,根据需要建立连接状态表,网络层保护强,应用层控制细,会话控制较弱。
4、防火墙术语
网关:在两个设备之间提供转发服务的系统。网关是互联网应用程序在两台主机之间处理流量的防火墙。这个术语是非常常见的。
DMZ非军事化区:为了配置管理方便,内部网中需要向外提供服务的服务器往往放在一个单独的网段,这个网段便是非军事化区。防火墙一般配备三块网卡,在配置时一般分别分别连接内部网,internet和DMZ。
吞吐量:网络中的数据是由一个个数据包组成,防火墙对每个数据包的处理要耗费资源。吞吐量是指在不丢包的情况下单位时间内通过防火墙的数据包数量。这是测量防火墙性能的重要指标。
最大连接数:和吞吐量一样,数字越大越好。但是最大连接数更贴近实际网络情况,网络中大多数连接是指所建立的一个虚拟通道。防火墙对每个连接的处理也好耗费资源,因此最大连接数成为考验防火墙这方面能力的指标。
数据包转发率:是指在所有安全规则配置正确的情况下,防火墙对数据流量的处理速度。
SSL:SSL(Secure Sockets Layer)是由Netscape公司开发的一套Internet数据安全协议,当前版本为3.0。它已被广泛地用于Web浏览器与服务器之间的身份认证和加密数据传输。SSL协议位于TCP/IP协议与各种应用层协议之间,为数据通讯提供安全支持。
网络地址转换:网络地址转换(NAT)是一种将一个IP地址域映射到另一个IP地址域技术,从而为终端主机提供透明路由。NAT包括静态网络地址转换、动态网络地址转换、网络地址及端口转换、动态网络地址及端口转换、端口映射等。NAT常用于私有地址域与公用地址域的转换以解决IP地址匮乏问题。在防火墙上实现NAT后,可以隐藏受保护网络的内部拓扑结构,在一定程度上提高网络的安全性。如果反向NAT提供动态网络地址及端口转换功能,还可以实现负载均衡等功能。
堡垒主机:一种被强化的可以防御进攻的计算机,被暴露于因特网之上,作为进入内部网络的一个检查点,以达到把整个网络的安全问题集中在某个主机上解决,从而省时省力,不用考虑其它主机的安全的目的。
二、市场上常见的硬件防火墙
(1)NetScreen 208 Firewall
NetScreen科技公司推出的NetScreen防火墙产品是一种新型的网络安全硬件产品。NetScreen采用内置的ASIC技术,其安全设备具有低延时、高效的IPSec加密和防火墙功能,可以无缝地部署到任何网络。设备安装和操控也是非常容易,可以通过多种管理界面包括内置的WebUI界面、命令行界面或NetScreen中央管理方案进行管理。NetScreen将所有功能集成于单一硬件产品中,它不仅易于安装和管理,而且能够提供更高可靠性和安全性。由于NetScreen设备没有其它品牌产品对硬盘驱动器所存在的稳定性问题,所以它是对在线时间要求极高的用户的最佳方案。采用NetScreen设备,只需要对防火墙、VPN和流量管理功能进行配置和管理,减省了配置另外的硬件和复杂性操作系统的需要。这个做法缩短了安装和管理的时间,并在防范安全漏洞的工作上,省略设置的步骤。NetScreen-100 Firewall比适合中型企业的网络安全需求。
(2)Cisco Secure PIX 515-E Firewall
Cisco Secure PIX防火墙是Cisco防火墙家族中的专用防火墙设施。Cisco Secure PIX 515-E防火墙系通过端到端安全服务的有机组合,提供了很高的安全性。适合那些仅需要与自己企业网进行双向通信的远程站点,或由企业网在自己的企业防火墙上提供所有的Web服务的情况。Cisco Secure PIX 515-E与普通的CPU密集型专用代理服务器(对应用级的每一个数据包都要进行大量处理)不同,Cisco Secure PIX 515-E防火墙采用非UNIX、安全、实时的内置系统。可提供扩展和重新配置IP网络的特性,同时不会引起IP地址短缺问题。NAT既可利用现有IP地址,也可利用Internet指定号码机构[IANA]预留池[RFC.1918]规定的地址来实现这一特性。Cisco Secure PIX 515-E还可根据需要有选择性地允许地址是否进行转化。CISCO保证NAT将同所有其它的PIX防火墙特性(如多媒体应用支持)共同工作。Cisco Secure PIX 515-E Firewall比适合中小型企业的网络安全需求。
(3)天融信网络卫士NGFW4000-S防火墙
北京天融信公司的网络卫士是我国第一套自主版权的防火墙系统,目前在我国电信、电子、教育、科研等单位广泛使用。它由防火墙和管理器组成。网络卫士NGFW4000-S防火墙是我国首创的核检测防火墙,更加安全更加稳定。网络卫士NGFW4000-S防火墙系统集中了包过滤防火墙、应用代理、网络地址转换(NAT)、用户身份鉴别、虚拟专用网、Web页面保护、用户权限控制、安全审计、攻击检测、流量控制与计费等功能,可以为不同类型的Internet接入网络提供全方位的网络安全服务。网络卫士防火墙系统是中国人自己设计的,因此管理界面完全是中文化的,使管理工作更加方便,网络卫士NGFW4000-S防火墙的管理界面是所有防火墙中最直观的。网络卫士NGFW4000-S防火墙比适合中型企业的网络安全需求。
(4)东软NetEye 4032防火墙
NetEye 4032防火墙是NetEye防火墙系列中的最新版本,该系统在性能,可靠性,管理性等方面大大提高。其基于状态包过滤的流过滤体系结构,保证从数据链路层到应用层的完全高性能过滤,可以进行应用级插件的及时升级,攻击方式的及时响应,实现动态的保障网络安全。NetEye防火墙4032对流过滤引擎进行了优化,进一步提高了性能和稳定性,同时丰富了应用级插件、安全防御插件,并且提升了开发相应插件的速度。网络安全本身是一个动态的,其变化非常迅速,每天都有可能有新的攻击方式产生。安全策略必须能够随着攻击方式的产生而进行动态的调整,这样才能够动态的保护网络的安全。基于状态包过滤的流过滤体系结构,具有动态保护网络安全的特性,使NetEye防火墙能够有效的抵御各种新的攻击,动态保障网络安全。东软NetEye 4032防火墙比适合中小型企业的网络安全需求。
三、防火墙的基本配置
下面我以国内防火墙第一品牌天融信NGFW 4000为例给各位讲解一下在一个典型的网络环境中应该如何来配置防火墙。
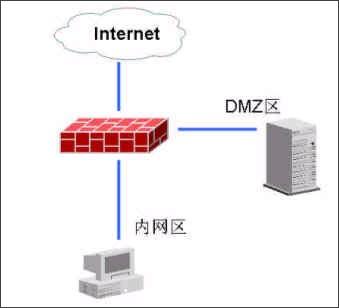
图5:网络拓扑结构
NGFW4000有3个标准端口,其中一个接外网(Internet网),一个接内网,一个接DMZ区,在DMZ区中有网络服务器。安装防火墙所要达到的效果是:内网区的电脑可以任意访问外网,可以访问DMZ中指定的网络服务器,Internet网和DMZ的电脑不能访问内网;Internet网可以访问DMZ中的服务器。
1、配置管理端口
天融信网络卫士NGFW4000防火墙是由防火墙和管理器组成的,管理防火墙都是通过网络中的一台电脑来实现的。防火墙默认情况下,3个口都不是管理端口,所以我们先要通过串口把天融信网络卫士NGFW4000防火墙与我们的电脑连接起来,给防火墙指定一个管理端口,以后对防火墙的设置就可以通过远程来实现了。
使用一条串口线把电脑的串口(COM1)与NGFW4000防火墙的console口连接起来,启动电脑的"超级终端",端口选择COM1,通信参数设置为每秒位数9600,数据位8,奇偶校验无,停止位1,数据流控制无。进入超级终端的界面,输入防火墙的密码进入命令行格式。
定义管理口:if eth1 XXX.XXX.XXX.XXX 255.255.255.0
修改管理口的GUI登录权限: fire client add topsec -t gui -a 外网 -i 0.0.0.0-255.255.255.255
2、使用GUI管理软件配置防火墙
安装天融信防火墙GUI管理软件"TOPSEC集中管理器",并建立NGFW4000管理项目,输入防火墙管理端口的IP地址与说明。然后登录进入管理界面。
(1)定义网络区域
Internet(外网):接在eth0上,缺省访问策略为any(即缺省可读、可写),日志选项为空,禁止ping、GUI、telnet。
Intranet(内网):接在eth1上,缺省访问策略为none(不可读、不可写),日志选项为记录用户命令,允许ping、GUI、telnet。
DMZ区:接在eth2上, 缺省访问策略为none(不可读、不可写),日志选项为记录用户命令,禁止ping、GUI、telnet。
(2)定义网络对象
一个网络节点表示某个区域中的一台物理机器。它可以作为访问策略中的源和目的,也可以作为通信策略中的源和目的。网络节点同时可以作为地址映射的地址池使用,表示地址映射的实际机器,详细描述见通信策略。
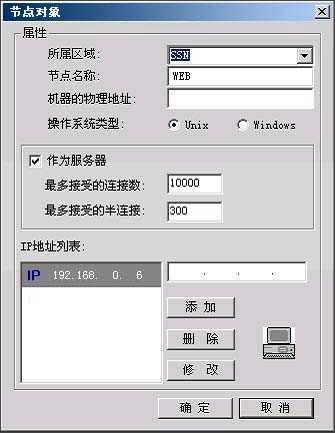
图6
子网表示一段连续的IP地址。可以作为策略的源或目的,还可以作为NAT的地址池使用。如果子网段中有已经被其他部门使用的IP,为了避免使用三个子网来描述技术部使用的IP地址,可以将这两个被其他部门占用的地址在例外地址中说明。
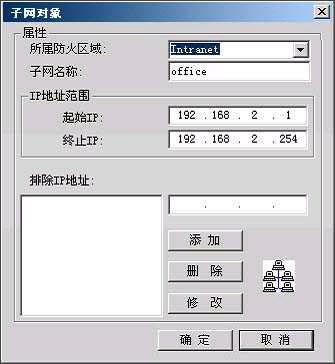
图7
为了配置访问策略,先定义特殊的节点与子网:
FTP_SERVER:代表FTP服务器,区域=DMZ,IP地址= XXX.XXX.XXX.XXX。
HTTP_SERVER:代表HTTP服务器,区域=DMZ,IP地址= XXX.XXX.XXX.XXX。
MAIL_SERVER:代表邮件服务器,区域=DMZ,IP地址= XXX.XXX.XXX.XXX。
V_SERVER:代表外网访问的虚拟服务器,区域=Internet,IP=防火墙IP地址。
inside:表示内网上的所有机器,区域=Intranet,起始地址=0.0.0.0,结束地址=255.255.255.255。
outside:表示外网上的所有机器,区域=Internet,起始地址=0.0.0.0,结束地址=255.255.255.255。
(3)配置访问策略
在DMZ区域中增加三条访问策略:
A、访问目的=FTP_SERVER,目的端口=TCP 21。源=inside,访问权限=读、写。源=outside,访问权限=读。这条配置表示内网的用户可以读、写FTP服务器上的文件,而外网的用户只能读文件,不能写文件。
B、访问目的=HTTP_SERVER,目的端口=TCP 80。源=inside+outside,访问权限=读、写。这条配置表示内网、外网的用户都可以访问HTTP服务器。
C、访问目的=MAIL_SERVER,目的端口=TCP 25,TCP 110。源=inside+outside,访问权限=读、写。这条配置表示内网、外网的用户都可以访问MAIL服务器。
(4)通信策略
由于内网的机器没有合法的IP地址,它们访问外网需要进行地址转换。当内部机器访问外部机器时,可以将其地址转换为防火墙的地址,也可以转换成某个地址池中的地址。增加一条通信策略,目的=outside,源=inside,方式=NAT,目的端口=所有端口。如果需要转换成某个地址池中的地址,则必须先在Internet中定义一个子网,地址范围就是地址池的范围,然后在通信策略中选择NAT方式,在地址池类型中选择刚才定义的地址池。
服务器也没有合法的IP地址,必须依靠防火墙做地址映射来提供对外服务。增加通信策略。
A、目的=V_SERVER,源=outside,通信方式=MAP,指定协议=TCP,端口映射21->21,目标机器=FTP_SERVER。
B、目的=V_SERVER,源=outside,通信方式=MAP,指定协议=TCP,端口映射80->80,目标机器=HTTP_SERVER。
C、目的=V_SERVER,源=outside,通信方式=MAP,指定协议=TCP,端口映射25->25,目标机器=MAIL_SERVER。
D、目的=V_SERVER,源=outside,通信方式=MAP,指定协议=TCP,端口映射110->110,目标机器=MAIL_SERVER。
(5)特殊端口
在防火墙默认的端口定义中没有我们所要用到的特殊端口,就需要我们手工的添加这些特殊端口了。在防火墙集中管理器中选择"高级管理">"特殊对象">"特殊端口",将弹出特殊端口的定义界面,点"定义新对象",输入特殊端口号与定义区域即可。
(6)其他配置
最后进入"工具"选项,定义防火墙的管理员、权限以及与IDS的联动等。(图8)
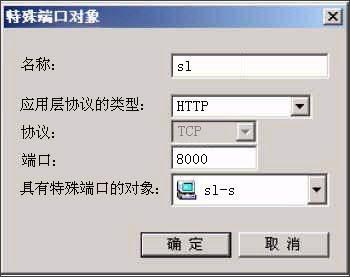
图8
四、防火墙对比
在了解了防火墙的工作原理及基本配置之后,下面给大家介绍一下NetScreen 208、Cisco PIX 515E、NGFW 4000-S、NetEye 4032这四款市场上最常见的硬件防火墙在基本性能、操作管理与市场价格上的比较。
防火墙
NetScreen208
CiscoPIX515E
NGFW4000-S
NetEye4032
核心技术
状态检测
状态检测
核检测
状态检测
产品类型
ASIC硬件
硬件设备
硬件设备
硬件设备
工作模式(路由模式、桥模式、混合模式)
路由模式、桥模式
路由模式、桥模式
路由模式、桥模式、
混合模式
路由模式、桥模式
并发连接数
130000
130000
600000
300000
网络吞吐量
550M
170M
100M
200M
最大支持网络接口
8个
6个
12个
8个
操作系统
ScreenOS
专用操作系统
专用操作系统
专用操作系统
管理方式
串口、CLI、Telnet、Web、GUI
串口、Telnet、Web、GUI
串口、Telnet、Web、GUI
串口、Telnet、GUI
市场报价
142,000RMB
80,000RMB
138,000RMB
148,000RMB
AMD adds 32-, 64-bit embedded processors
Feb. 12, 2007
AMD has introduced several new versions of its Geode LX processor, and has added a "low power" version of its 35-Watt dual-core Athlon 64 X2 to its embedded roadmap. Additionally, the company is offering three new reference designs, including an ATCA blade, a SOHO NAS server, and an "ultra-value client."
AMD‘s slew of embedded processor news announcements were timed to coincide with the opening of the Embedded World Exhibition & Conference in Germany on Feb. 12.
New Geode LX models
AMD has added two new models to itsGeode LX SoC (system-on-chip) family, which previously consisted only of the 500MHz LX800@0.9 part. The new Geode LX900@1.5 model runs at a slightly higher voltage -- and consumes a little more power -- while the LX700 runs slightly cooler.
CPU Clock Typical Power TDP
LX700 433MHz 1.3W 3.1W
LX800 500MHz 1.8W 3.6W
LX900 600MHz 2.6W 5.1W
AMD‘s Geode LX line

Geode LX function
block diagram
(Click to enlarge)
The Geode LX was the first and only embedded processor designed by AMD after itacquired the Geode line from National Semiconductor in 2003. Fabbed on a 0.13-micron process, the chip has an x86/x87 compatible core, and integrates typical northbridge functions such as memory and graphics controllers. It is designed for use with AMD‘s CSCS5536 companion chip.
New RDKs
Also new from AMD are a pair of "reference design kits" (RDKs) based on its Geode LX SoC line, and one new reference design based on dual Opteron processors. The designs include: SOHO NAS (network attached storage for small office, home offices) -- A Linux-based hardware/software reference design said to support the sharing of home movies, music, and other forms of data while providing redundancy, back-up, and security features. The design‘s hardware features include gigabit Ethernet, board-level SATA, a 4-drive bay storage system option, and an integrated memory controller. According to Jeff Chu, AMD‘s division manager for embedded, "It‘s good at handling data movement -- in the range of 10-15Mbps throughput. That‘s above some of the RISC-based designs that are out there." Chu also noted that a third-party customer offers a BSD stack for the design.
Geode LX UVC (ultra-value client) -- Described as a fifth-generation RDK for designers of low-cost PCs, SBCs (single-board computers), POS (point-of-sales/services) devices, corporate thin clients, network appliances, and kiosks, the RDK includes an optical drive and a hard drive. It supports Linux, Windows CE, or Windows XP, Chu said.
ATCA blade reference design -- Designed in partnership with Pinnacle Data Systems (PDS), the design supports Dual "2P" Opteron processors, using a Broadcom chipset. As for OS support, Chu said, "We always work with MontaVista and Wind River on Carrier Grade Linux stuff, and lately we‘ve been working with FSMLabs on real-time Linux support as well. We‘re committed to the open platform approach, and are enabling our customers to make the choices they need to make."
Early RDK customers reportedly include Advansus, Advantech, ICP, and Liteon.
Embedded roadmap additions
Finally, AMD has announced the addition of two semi-existing processor designs to its AMD64 Longevity Program, which guarantees at least five years of production availability. Both fit AMD‘s relatively new AM2 motherboard socket, and thus support DDR2 memory. And, for telecom applications such as ATCA and MicroATCA boards, both support ECC (error checking and correction) memory, Chu said.
One is the 3400+ model in AMD‘s line of "low power, small form factor" dual-core Athlon 64 X2 processors. With a TDP (thermal design power) of only 35 Watts, this part runs considerably cooler than the standard 85 Watt and "low power" 65 Watt parts in AMD‘s normal Athlon 64 X2 line. Additionally, Chu notes that the chip has a 20 Watt low-power state, and can be configured via BIOS settings to stay within that envelope.
The Athlon 64 X2 3400+ is "semi-new" because in the past, AMD appears to have marketed the chip with a slightly faster clock rating as the 64 X2 Dual-Core 3800+ (ADD3800IAT5CU for OEMs, and ADD3800CUBOX for retail). Although "shipping" for nearly a year, short supplies have resulted in street prices upwards of $400 for the retail box version. Thus, AMD appears to have settled for a slower clock speed, and added the part to its Longevity Program to reassure customers of its commitment to the part.
The other chip newly added to the AMD64 Longevity Program is the Sempron 3000+ (SDD3000CNBOX), a relatively inexpensive single-core part that also has a TDP of 35 Watts.
Availability
The Geode LX900 and LX700 appear to be available now. The three RDKs have all shipped to customers, according to AMD. The Athlon 64 X2 3400+ is said to be available, although as of publication time, it had not yet been added to AMD‘s processor feature comparison chart. The Sempron 3000+ is shipping now.
Earlier this month,AMD added its dual-core Turion 64 X2 Model TL-52 and single-core Mobile AMD Sempron 3500+ to the AMD64 Longevity Program. Meanwhile, competitor Intel is rumored to be prepping aPentium M-based SoC that could compete with Geode processors.
Related Stories:AMD aims Geode LX at "x86 everywhere"
Intel prepping Pentium M-based SoC?
Geode finds a new home at AMD
Single-chip x86-compatible chipset runs Linux
AMD offers free Geode-based EPIC SBC design
Mobile 64-bit chips arrive on AMD‘s embedded roadmap
Intel, AMD drop out of mobile handset chipset game
(Click here for further information)

Dot Hill has pioneered a revolutionary new storage architecture for the Volume Storage Market: the Rapid Evolution Storage Architecture™. This highly modular, highly dynamic system is designed to rapidly evolve and support OEM technology, enabling OEMs to quickly achieve sustainable competitive advantage in the Volume Storage Market.
The Rapid Evolution Storage Architecture, or R/Evolution™ Architecture, delivers the high levels of performance, storage density, time-to-market leadership and - most importantly - configuration flexibility required in the Volume Storage Market. Using modular and bladed components, the R/Evolution Architecture provides OEMs with a "Configure-to-Product" model (not just "configure-to-order") that lets them customize Volume Storage Market solutions quickly, easily and precisely. This unique model revolutionizes how OEMs bring storage products to market by ensuring opportunities for product differentiation, even between different companies that simultaneously OEM product from Dot Hill. Important benefits of the R/Evolution Architecture include: Significantly faster time-to-market that allows OEMs to quickly roll out highly targeted Volume Storage Market solutions and preempt their competition. Lower OEM costs at every stage of new product introduction. These substantial development and introduction savings help enable market leading pricing for Volume Storage Markets and enhance OEM profitability. Faster, easier integration of OEM value-added technologies or capabilities, providing greater opportunities for differentiation in the Volume Storage Market.
Key Macro Trends Impacting the Volume Storage Market
The Volume Storage Market is under intense pressure. New regulatory requirements and evolving business demands are driving the need for Volume Storage Market solutions that hold down costs, yet deliver more and more enterprise-level features, capabilities and software. Why? Data from applications like file serving, disk-to-disk backup, short-term archiving and near-line storage of bulk data must be quickly and readily available to multiple users. Yet because this data is not always mission-critical, it is uneconomic to store it on high-availability, mission-critical storage systems with prohibitive per-GB-costs. In addition, regulations like Sarbanes-Oxley and HIPAA mandate the ability to rapidly access enormous quantities of financial and medical data. Although this data may be months or years old, nonetheless, tape archive is not a viable solution due to the extensive time required to restore from tape. Thus, tiered storage strategies—which seek to properly balance costs and capabilities in order to efficiently store this rapidly expanding pool of "in-between" data—are becoming critical in the Volume Storage Market.Below are key macro trends that are driving the Volume Storage Market: Tiered Storage - In the broad and highly diverse Volume Storage Market, one size does not fit all. Organizations need storage solutions that mix and match performance, availability, cost and capabilities to address the specific needs of each storage tier in the organization. In addition, new technologies and the application of existing/repackaged technologies, such as ILM (Information Lifecycle Management), D2D (Disk-To-Disk) backup, CAS (Content Addressable Storage), and CDP (Continuous Data Protection) are requiring greater flexibility and intelligence in every dimension of the storage solution…not just at the time of purchase, but over the lifetime of the storage solution. Thus, the increasing need for tiered storage that can evolve and adapt, efficiently and gracefully. Regulatory - New regulations such as SEC 17a-4, SarBox section 404 and HIPAA are driving new mission-critical, tiered storage strategies in every organization. Data such as financial information, medical records, and email correspondence must not only be tracked, protected and secured, but also must be globally available upon demand. Given the dynamic nature of these requirements, storage solutions with architectures that embrace modularity, "pay-as-you-go" economics and easy scalability/upgradeability throughout the product lifecycle are likely to work best for IT customers. Security - The ability to ensure trusted access to data is one of the factors driving enhanced intelligence, access control and authentication capabilities in the storage market. As in the networking and telecommunications industries, the ability to enhance security while still providing productive access for authorized users is vital for business success. Blades and Grids - The growth of blade servers and grid computing is driving new SAN (Storage Area Network) configurations and interface requirements. As the networks for communication, networking, cluster computing and storage move closer together, flexible, intelligent and "grid-aware" storage platforms are required. Storage platforms must be ready for this unified networking environment and provide a graceful path to moving/migrating between or across these varied networking requirements. More than hardware, this must include intelligent data and virtualization software services to deal with the myriad of combinations and configurations. Business Continuance - Ensuring that operations continue without disruption is a leading priority for IT organizations worldwide. This requirement has lead to an increased use of disk-based solutions for replication of data in remote sites for business continuance, using disk-to-disk (versus tape) for backup to make recovery instantaneous and using tiered disk-storage strategies for cost-effectively archiving data online in order to meet regulatory requirements. Object-Based Storage - Object-Based Storage (OBS) is vital to the next generation of file systems such as Microsoft‘s WinFS. OBS will require a new approach to storage access, security, intelligence and management. Without a solid, well conceived architecture, current storage solutions could have difficulty migrating to OBS technology. Thus, it‘s essential that Volume Market storage solutions have designs that can easily accommodate the new layers of capability and intelligence that manage not only the primary data, but the meta-data that will be vital to the next generation of optimized data access, search and retrieval. Disk Storage Growth - Disk storage is growing in three principal ways. First, the number of files generated by computers continues to grow at an accelerated rate. Second, customers are using formats that generate larger file sizes, so the same number of files takes up more disk space. Finally, files that previously were stored on tape are now being stored on disk for data protection and for regulatory purposes (due to access time requirements). These factors require not only more storage, but storage that is optimized (cost and performance) for each application.
Volume Market Storage Requirements
Five years ago, the storage market was much simpler. The very high end of the mainframe and mission-critical markets demanded the highest performance and availability. The Volume Storage Market supported work groups and non-mission critical applications, and the entry-level market was a collection of small/standalone systems that were very low cost, and not very functional.
Today the storage industry is much different. Although the volume of data continues to grow exponentially, enterprises are no longer willing to endlessly invest in high-end storage systems. Further, there is an ever-increasing volume of data that falls "in-between" these high-end, online storage systems (with their high cost-per-GB), and low-cost, high-capacity tape archival systems (with their slow, labor-intensive data retrievals). What‘s more, the availability, access, protection, security and performance requirements for this "in-between" data can vary greatly, depending on its particular use: Databases and e-commerce that require high performance, I/O-intensive application computing High-capacity, cost-effective storage to meet regulatory requirements Near-line archive of infrequently used data that nonetheless must be available at all times Cost-effective storage of data generated by email and office productivity applications
For IT managers, tiered storage offers a solution to this dilemma. Yet tiered storage solutions must do more than merely provide high capacity, optimal performance, low cost-per-GB and easy integration into established enterprise infrastructures. They must also be able to adapt and evolve rapidly so that they can deliver the optimal balance of cost/performance levels for every type of data. In short, the Volume Storage Market can be characterized by its overarching requirement for configuration flexibility. This requirement has made the Volume Storage Market the most challenging and exciting segment in the storage business. It also demands a much more modular and flexible architecture, one that can be quickly and cost effectively optimized to balance the various metrics that define storage solutions: Performance - IOPS (Inputs/Outputs per Second) and data rates (the speed at which the data is transferred during IOPS) are the two fundamental measurements of performance. These benchmark numbers are the basis for defining storage performance in the market. The ability to provide and optimize IOPS and data rates for key applications is vital to providing the right solution for each application. Manageability - The ability to control, configure, allocate and deploy storage resources is perhaps the greatest factor in the ultimate cost—and value—of a storage solution. Reducing human interactions and increasing automated/proactive operations are two key factors impacting overall efficiency and lowering total cost-of-ownership. Protection - New regulations and competitive requirements make the cost of data protection one of the key decision points in selecting any storage solution. Every level of the storage solution should offer various levels of data protection to meet the specific needs of each class of data. Cost - The market is segmented based on the cost to achieve desired levels of performance, manageability, protection, and density/capacity. Acquisition cost is most visible, but cost of ongoing operations/management has the greatest effect on total cost of ownership. Density/Capacity - Measurement of the number of disks that can fit into a standard unit of rack space. By maximizing density and capacity, IT departments can get more total IOPS and greater overall data throughput rates per individual rack. Storage Tiers - While one size does not fit all, one integrated storage strategy is vital to getting maximum value out of capital dollars invested. Tiered Storage provides the ability to integrate various storage personalities under a single architecture.
While the first five metrics apply to all segments of the storage market, the final metric—Storage Tiers—is unique to the Volume Storage Market. It is the critical factor for delivering the most cost effective solutions, optimized across a broad range of features, functionalities and capabilities. For OEMs, success in this arena lies in the ability to capitalize on a storage architecture that is modular and flexible enough to meet all of these widely varying demands—both when the solution is purchased and over the life of the solution. At the same time, the architecture must share core technologies so that it is completely interoperable across different configuration and iterations.
This is why Dot Hill has pioneered the Rapid Evolution Storage Architecture. It is a single, integrated storage platform that can deliver maximum configuration flexibility in Volume Market storage solutions. Its extreme modularity and "Configure-to-Product" model provide the ability to rapidly create solutions that can be selected by each OEM to meet the specific needs of their targeted markets and the positions they wish to claim. The Rapid Evolution Storage Architecture, or R/Evolution Architecture, not only allows OEMs to balance the features and capabilities so critical to success, it also provides the tools to optimize for only one of the metrics, or all six metrics of the Volume Storage Market.

Rapid Evolution Storage Architecture
OEMs require a Volume Market storage platform that gives them market flexibility and product adaptability so they can deliver storage solutions that successfully address the market factors previously outlined. Further, their solutions must offer their customers investment protection, with the ability to easily and cost effectively adapt as new demands and/or requirements are placed upon their storage strategies. The R/Evolution Architecture does this, providing: Core technologies shared across chassis platforms Highly modular, blade-driven architecture Easy integration of OEM value-add/storage applications Advanced file and storage management services Common spares and field upgrades
These foundational attributes of the R/Evolution Architecture are further enhanced by Dot Hill‘s corporate culture of responsiveness and flexibility. As a partner, Dot Hill has a proven track record of supporting innovative business models in order to meet the needs of its OEM customers, as well as their end-user customers. The net result: the benefits of off-the-shelf pricing and flexibility, combined with the ability to radically customize the features and functions of storage solutions... during development and after deployment.

The R/Evolution Architecture provides a roadmap for the future of the many market factors driving storage today. Its common technology core supports a dynamic path to expanding performance, capabilities, capacity and manageability, protecting against obsolescence and allowing OEMs and their customers to easily and affordably meet evolving storage needs over the lifetimes of their storage systems. This provides a higher level of investment protection, without the overhead inherent in solutions that don‘t use the R/Evolution Architecture. In sum, the products that OEMs build will now be as dynamic as the markets they work in…today and tomorrow.
Tiered Storage Modules (TSM)
The R/Evolution Architecture Tiered Storage Modules support RAID, SBOD (Switched BOD) and JBOD configurations that deliver some of the industry‘s highest levels of drive density and the most efficient use of standard rack space. The R/Evolution Architecture supports multiple chassis configurations and can support Fibre Channel (FC), Serial-Attached SCSI (SAS) and Serial ATA (SATA) drives, all in a single system…all in the same rack. This flexibility allows OEMs to precisely balance the metrics of cost, protection and performance in their Volume Storage Market solutions.
The R/Evolution Architecture provides 20% more disk drives in a typical rack. This means greater capacity, better performance and greater cost effectiveness, which translates into higher data rates/IOPS-per-rack in the data center.

Host Iinteface Modules (HIMS)
HIMs are one of the components of the PDC module. A HIM allows the controller connection to the host to be changed between interfaces. Initially, R/Evolution Architecture will support 4Gb FC, 3Gb SAS and 1GbE iSCSI connectivity. In addition, the HIM offers the ability to easily add new interfaces such as 10Gb iSCSI, 8Gb FC, Infiniband and other host interconnections. This allows OEMs and their customers to readily anticipate and adapt to the convergence of storage interfaces.

Performance Data Controllers (PDCS)
The core controller technology of R/Evolution Architecture provides performance where and when it is needed. The flexible design is capable of moving data at up 1.5GB/s and at over 200K IOPS, delivering up to twice the performance of competitive Volume Storage Market solutions. With multiple performance and protection parameters available, the PDCs provide a modular approach that allow OEMs to finely balance cost and performance metrics. They also provide post-deployment adaptability for end user customers. The PDC supports multiple CPU speeds and cache increments from 512MB to 2GB per controller. The PDC is comprised of three components: the RAID I/O module, the Host Interface Module (HIM) and the Drive Module (DM). The RAID I/O module is the RAID engine for the R/Evolution Architecture. Not only is it a highly flexible software core for RAID capabilities, the RAID I/0 also hosts the Dot Hill Storage Services software and includes the management engine for the R/Evolution Architecture. Dot Hill‘s unique PowerFlex RAID technology and our patent-pending SimulCache provide industry-leading write performance. In addition, PowerFlex RAID allows the flexibility to run either Dot Hill or OEM RAID cores to improve OEM integration. (The HIMs and DMs are discussed in other sections.)

Drive Modules (DMS)
DMs are one of the components of the PDC module. A DM provides the flexible option for adding, changing or expanding new drive interfaces in a single architecture.

Storage Application Blades (SABS)
The high speed back plane of the R/Evolution Architecture supports multiple types of blades, including server blades, cluster fabric blades, and other OEM application hardware blades. Using industry standard interfaces, SABs of the R/Evolution Architecture can adapt to the needs of the environment, providing differentiation opportunities as well as investment protection. OEMs can use these blades to host value-added software and build solutions that target multiple verticals and/or enterprise applications…all on the same core platform. In this era of commoditization and shrinking margins, SABs may provide the best opportunity for solution differentiation and greater profitability.
Dot Hill Storage Services (DSS)
Snapshots - Snapshots provide the ability to create a Point-In-Time copy of a disk volume. Dot Hill Storage Services can create full snapshots of volumes or delta snaps of recent changes. It provides customers the ability to roll-back to any point in time. These disk images can be used to replicate data, create a new working volume or as a business continuance volume Remote Replication - One of the keys to ensuring business continuance is the ability to protect data over distances in case of local/regional events such as fire, hurricane or earthquake. Dot Hill Storage Services provides the ability to replicate and protect data over any IP network to anywhere across the globe. Remote volumes can be read, read-write and boot volumes if the OS permits remote boot devices RAIDar Manager - Dot Hill‘s RAIDar Manager provides the ability to create, configure and control disk volumes dynamically without interrupting operations. It provides users with complete control and reporting tools over every aspect of their storage system Storage Presentation Services - Dot Hill‘s storage presentation services provide the ability to present storage in a variety of ways. It enables file services, storage virtualization, resource management, cross-vendor APIs, flexible software and feature licensing, as well as support for industry standards such as SMI-S. These services enable OEMs to build solutions that are tightly integrated into existing product lines and create unique value-add.

The R/Evolution Architecture Advantage
At the heart of the R/Evolution Architecture is our highly modular, blade-driven design. This "modular core" provides a comprehensive range of configuration options to OEMs, as shown in the diagram below. Each module component allows OEMs to craft a personality and target application for their solutions, all with a low-cost, build-to-order model. In addition, this highly modular, blade-driven design provides easy, future upgradeability for OEM end-user customers, ensuring investment protection and long-term ROI.
The ability to select specific module components and options within the R/Evolution Architecture makes possible virtual "off-the-shelf" solutions that target various sub-segments of the Volume Storage Market. In addition, it allows OEMs to create highly differentiated solutions within their own niche segments. The diagrams shown here and the chart further down demonstrate how various configurations can be quickly identified, illustrating that even though one size does not fit all in the Volume Storage Market, one architecture can…and does.

Finally, the R/Evolution Architecture not only meets the needs of the Volume Storage Market today, it provides a compelling roadmap to the future. As the storage market continues to evolve on a daily basis, most changes will be small and incremental. Yet even if they are sudden and dramatic, the bladed, modular, interchangeable nature of the R/Evolution Architecture will allow OEMs and their customers to rapidly and painlessly adapt to these changes. One of the best examples is the change in storage networking performance. While a major jump in performance may send some market players into a frenzy of "market-tecure" or "slide-ware" in order to define how they will cope with the new changes, the R/Evolution Architecture provides OEMs with a simple solution that will allow them to effectively manage these changes in advance.

Business Advantage For OEMs: R/Evolution Architecture + Dot Hill
Dot Hill provides a revolution in how OEM‘s bring storage products to market. The R/Evolution Architecture helps OEMs accelerate their time-to-market and reduce development costs, while providing an integrated storage platform that makes it easier to incorporate value-added offerings that enhance differentiation and increase profitability.
Time-to-Market Advantage
The R/Evolution Architecture creates a single design core that can be used across multiple families of products. The products can bridge different chassis sizes, host connections, drive types and price points. It provides a common parts and service capability across those product families. In short, the R/Evolution Architecture enables OEMs to capitalize on a "Configure-to-Product" model to dramatically reduce time to market.
Development Savings
The R/Evolution Architecture lowers the cost of new product introduction at every stage for OEMs—from concept to design to manufacturing. This enables substantial development savings for OEMs, delivers market leading pricing for Volume Storage Markets and enhances OEM profitability. But the advantages are not just about products. They extend to Dot Hill‘s flexible business model and ability to support any level of joint development and go-to-market model on a global basis. This allows OEMs to focus on the part of the program/product that creates the maximum value for OEMs and their customers.
Storage Integration Platform
The R/Evolution Architecture provides a host platform for OEM value-add applications. As software value-add continues to define differentiation in the market, Dot Hill is committed to providing the ideal Volume Market storage platform to enable these profitable solutions. The combination of Dot Hill‘s core Storage Services software and OEM value-add applications can create a powerful force in the market.
Summary
As the Volume Storage Market continues to evolve, Dot Hill and its R/Evolution Architecture will continue to meet the needs of OEMs and their customers. The ever-increasing need for modularity, flexibility, performance and enterprise data management features will only grow. The R/Evolution Architecture is the integrated platform that provides a complete, flexible template for OEMs to build winning solutions for every segment of the Volume Storage Market, and for their customers to have access to simple, cost-effective upgrades in the future, protecting their investments.
Download PDF Version (4.5MB PDF)
R/Evolution Demo (8MB Zip)
Why Dot Hill? (472KB PDF)
The 2730 Data Sheet (504KB PDF)
http://www.dothill.com/
The Linley Wire
Independent Analysis of the Networking-Silicon Industry
Volume 5, Issue 8
April 20, 2005

Editor: Linley Gwennap
Contributors: Bob Wheeler, Jag Bolaria, Sanjay Iyer
In This Issue
NPU Market Sees Broad-Based ExpansionAlacritech Blocks Microsoft ChimneyAdaptec Exits Chip BusinessIDT Unveils Interconnect StrategyNews In BriefSeminar Program Updates
A Guide to Storage Networking Silicon is now available for immediate delivery. Get up-to-date information on storage networking, including SAN, NAS, and IP storage. New in this edition is coverage of Fibre Channel and SAS/SATA devices, an emerging category of storage processors that is starting to heat up. For more information, visit ourweb site.
NPU Market Sees Broad-Based Expansion
The Linley Group has completed its survey of the network-processor market for 2004. Our final data shows NPU revenue grew an outstanding 61% over 2003 to reach $145 million. The market even managed to grow slightly in 2H04 over 1H04, despite market-leaders AMCC and Intel suffering revenue declines. The inventory correction seen across the broader markets slowed, but did not stall, NPU expansion.
Our data also reveals that, with only one exception, every vendor increased its NPU revenue in 2004. Intel contributed the most dollars to the market’s growth, gaining 6% market share as a result. Despite losing an equal amount of share, AMCC still increased its NPU revenue by more than any vendor except Intel. Thanks to initial shipments of its APP500 family, Agere gained share while nearly tripling its NPU revenue.

Hifn increased revenue from the former IBM PowerNP line by about 40%, resulting in a small share loss. But with first-year revenue surpassing the amount Hifn paid for the product line, the company should be very pleased with its results. Vitesse continues to defy gravity, maintaining share without active product development. Although Vitesse clearly has the most profitable NPU business of any vendor, it will begin losing share as current design wins reach end of life. As the only vendor to experience declining NPU revenue in 2004, Freescale is already seeing its discontinued C-Port line ramp down.
Startups Wintegra and EZchip showed strong growth, thanks to their focus on the underserved access and 10Gbps markets, respectively. Wintegra was the leading NPU startup in 2004, roughly doubling its revenue over 2003. EZchip nearly tripled its revenue in 2004, but its share of the overall market remained below 5% in 2H04.
Although 2004 closed stronger than anticipated, we continue to believe that NPU growth will slow this year. We now expect the NPU market to reach about $175 million in 2005. This slower growth rate should be sustainable through 2008, however, as NPUs continue to replace ASICs and fixed-function ASSPs. —BW
Complete coverage of the NPU market appears in our reportA Guide to Network Processors.
Alacritech Blocks Microsoft Chimney
The Vatican may be blowing smoke, but Microsoft’s TCP Chimney isn’t, after U.S. District Court judge Jeffrey White granted Alacritech a preliminary injunction preventing Microsoft from developing or distributing its TCP offload software. A pioneer in the development of TCP offload, Alacritech had sued Microsoft for infringing on its patent 6,697,868, one of several patents that Alacritech has been granted on its technology.
Several companies have developed TCP offload chips, ranging from giants such as Broadcom to startups such as Astute and Silverback. TCP offload is useful for Gigabit Ethernet connections, reducing the load on the main server processor, and highly recommended for 10 Gigabit Ethernet. Most of these chips don’t work with Microsoft Windows today but will work with TCP Chimney, due to be released in mid-2005 as part of the Scalable Networking Pack for Windows Server 2003 and also as part of the “Longhorn” operating system in 2006.
Alacritech’s legal action may stall these releases or cause Microsoft to remove TCP Chimney from the code. Microsoft has already been forced to strip TCP Chimney from its beta releases and is forbidden from doing internal testing or development. If this situation continues for months or years, it would severely limit the revenue potential of the chip companies in this space and slow the adoption of 10G Ethernet.
Microsoft has few options. It can appeal the injunction, but such appeals are rarely won. It can hope to prevail in a full trial, but the 868 patent clearly bears on TCP Chimney, and Judge White has already rejected Microsoft’s claims that the patent is invalidated by several cases of prior art. Unless Microsoft comes up with additional instances of prior art, its chances of winning at trial are poor. Even if it does eventually prevail, its TCP offload plans could be in limbo for several months, pushing TCP Chimney out of the Longhorn release and beyond the window for 10G Ethernet deployment.
We expect Microsoft to instead settle the case. Because Alacritech disclosed its TCP technology to Microsoft in 1999 under a non-disclosure agreement, Microsoft could be found liable of “willful violation.” Such a finding would result in triple damages, an amount that could easily exceed $100 million. The software giant would be better off cutting a big check to Alacritech instead of stalling the adoption of TCP offload technology. —LG
Additional coverage of TCP Chimney and TCP offload chips appears in our recent reportA Guide to Gigabit and 10G Ethernet Silicon.
Adaptec Exits Chip Business
Last week, Adaptec and Vitesse took the wraps off an alliance that positions Vitesse as a preferred SAS silicon supplier to Adaptec. The first products from this alliance—the single-chip VSC7250 and VSC7251 RAID controllers—combine Adaptec’s software and RAID 5/6 hardware accelerators with Vitesse’s CPU and SAS PHY technology to deliver up to 4GB/s RAID throughput. The VSC7250, which provides 8 SAS ports and uses an eight-lane PCI Express interface, lists for $64 in high volumes; the VSC7251, with four SAS ports and a four-lane PCI Express interface, lists at an affordable $46. These low-priced RAID controllers address a potentially huge SOHO and SMB market. Both devices will sample in May.
In a separate development, Adaptec struck a deal to outsource development of a 10Gbps iSCSI controller to startup ServerEngines, instead of using the in-house team from its Platys acquisition. The 10Gbps controller will be compatible with Adaptec’s current Vega controllers. Like the Vitesse deal, the ServerEngines agreement includes the transfer of some Adaptec engineers and intellectual property to jump-start development.
Taken together, these two deals signal the end of chip development at Adaptec. Perhaps not coincidentally, Ahmet Houssein recently left his role as GM of Adaptec’s Storage Solutions group, which developed SAS and iSCSI chips, to become CEO of storage-processor startup Silverback. Adaptec’s move acknowledges that storage silicon is on its way to becoming a commodity, moving the value to software, interoperability, and support. While semiconductor vendors such as AMCC and LSI juggle a storage-systems business alongside their primary semiconductor business, Adaptec has wisely chosen to drop silicon development and focus only on systems and software; its new priorities mean that the company can expand its storage-systems business, as it did by acquiring SAN-server vendor Snap Appliance. Adaptec’s chipless strategy is a boon to Vitesse and ServerWorks, who gain a special relationship with a seasoned storage vendor. —SI
Complete coverage of storage processors appears in our reportA Guide to Storage Networking Silicon.
IDT Unveils Interconnect Strategy
This week, IDT announced plans to offer a family of RapidIO switches, which it expects to sample in early 2006. These switches will be useful in connecting clusters of DSP and embedded processors in wireless infrastructure and similar applications. Previously, IDT had announced SPI-4 bridges and PCI Express bridges and switches, as well as its plans to offer components for ASI. The combination of these products represents a concerted effort to address board-level and system-level interconnect beyond the PC.
IDT has focused on developing several board-level interconnects for specific market segments but a common system-level interconnect. The company has not announced plans to offer system-to-system interconnect products, however. IDT appears to have segmented board-level requirements among networking, wireless infrastructure, and embedded applications. The common board-level interconnect technologies used in these applications are SPI-4, RapidIO, and PCI Express/RapidIO, respectively. IDT plans to offer a bridge and switch product for each of these technologies. The boards using these technologies are then connected over the system backplane using ASI. The company has yet to announce details on its ASI products.
IDT is embarking on a clear strategy, which offers it the potential to establish leadership in the rapidly growing interconnect market. A critical factor for this strategy, however, is the timing for the adoption of new technologies such as RapidIO and ASI. Additionally, the company must execute on several development fronts before it can translate the strategy into real revenue. —JB
Complete coverage of IDT’s newest products and other interconnect products will occur at our live seminar event on April 27 (see below).
News In Brief
Xelerated has closed a $17 million third round of funding. This round included new investors Accel Partners and Amadeus Capital Partners. Xelerated says the new funding should carry the company to profitability, which is expected in 2006. Separately, Xelerated says it has taped out its X11 second-generation network processor and that early samples will reach customers in July. Considering that Xelerated originally targeted the OC-768 market, the startup deserves a great deal of credit for surviving the NPU market consolidation. —BW
Complete coverage of Xelerated appears in our reportA Guide to Network Processors.
Earlier this month, TeraChip announced that it had raised an additional $7 million from Accel Partners and Benchmark Capital. The company has also added a new CEO, Rod Kay, replacing Micha Zeiger, who takes over as the Chairman of the board and CTO. Now, the startup needs a new direction and flawless execution to establish a market position. With the latest funding, TeraChip will need to leverage its existing architecture to create a new family of fabric products that is differentiated from existing products and targets a developing market: a tall order for a startup that has yet to make its mark. —JB
Seminar Program Updates
Join us on April 27 in San Jose, CA for a free one-day seminar on Fabrics and High-Speed Interconnects. This technical program will consist of a tutorial by Jag Bolaria, senior analyst at The Linley Group, followed by three in-depth sessions packed with information from industry leaders.
New additions to the technical program:
* Ron Wilson, Semiconductor Editor, EE Times, "EE Times Backplane Survey Results"
Session I: Board Level Interconnects:
* Delfin Rodillas, Staff System Architect, Xilinx, "FPGA Serial Interconnects"
* Brad Booth, Chair, IEEE P802.3an Task Force, will join the panel discussion
Session II: Panel Discussion: Selecting the Future Form Factor
This panel will include the leading proponents of the various form factors available in the industry, including ATCA, SIOM, VME, and more.
Panelists include: Eddie Reid, Chair, PCI-SIG PCI Express, SIOM; Rob Davidson, VP of Marketing, ATCA; Melissa Heckman, Vice Chair of the VSO, VME; Andrew Alleman, Systems Architect, Radisys
Session III: System or Advanced Interconnects
* David Formisano, Technical Marketing Manager, Intel, "Connecting the Modular Communications Platform: Standard Fabrics and Interconnects"
* Ed Bollet, Product Director, InfiniBand, will join the panel discussion
For the full program of topics and speakers, visit ourweb site.
The seminar is free to qualified individuals who register early. Non-qualified registrants will be charged a fee. For complete details and registration information, visit theseminar page.
This event is sponsored by IDT, StarGen, Sandburst, Intel, Xilinx, and InfiniBand Trade Association.
To receive The Linley Wire via e-mail,click here
About The Linley Wire
http://www.linleygroup.com/Reports/storage_guide.html
全方位讲解硬件防火墙的选择(多图)
http://www.sina.com.cn 2005年01月05日 13:48 天极网
文/tanker
防火墙是指设置在不同网络(如可信任的企业内部网和不可信的公共网)或网络安全域之间的一系列部件的组合。它是不同网络或网络安全域之间信息的唯一出入口,通过监测、限制、更改跨越防火墙的数据流,尽可能地对外部屏蔽网络内部的信息、结构和运行状况,有选择地接受外部访问,对内部强化设备监管、控制对服务器与外部网络的访问,在被保护网络和外部网络之间架起一道屏障,以防止发生不可预测的、潜在的破坏性侵入。防火墙有两种,硬件防火墙和软件防火墙,他们都能起到保护作用并筛选出网络上的攻击者。在这里 主要给大家介绍一下我们在企业网络安全实际运用中所常见的硬件防火墙。
一、防火墙基础原理
1、防火墙技术
防火墙通常使用的安全控制手段主要有包过滤、状态检测、代理服务。下面,我们将介绍这些手段的工作机理及特点,并介绍一些防火墙的主流产品。
包过滤技术是一种简单、有效的安全控制技术,它通过在网络间相互连接的设备上加载允许、禁止来自某些特定的源地址、目的地址、TCP端口号等规则,对通过设备的数据包进行检查,限制数据包进出内部网络。包过滤的最大优点是对用户透明,传输性能高。但由于安全控制层次在网络层、传输层,安全控制的力度也只限于源地址、目的地址和端口号,因而只能进行较为初步的安全控制,对于恶意的拥塞攻击、内存覆盖攻击或病毒等高层次的攻击手段,则无能为力。
状态检测是比包过滤更为有效的安全控制方法。对新建的应用连接,状态检测检查预先设置的安全规则,允许符合规则的连接通过,并在内存中记录下该连接的相关信息,生成状态表。对该连接的后续数据包,只要符合状态表,就可以通过。这种方式的好处在于:由于不需要对每个数据包进行规则检查,而是一个连接的后续数据包(通常是大量的数据包)通过散列算法,直接进行状态检查,从而使得性能得到了较大提高;而且,由于状态表是动态的,因而可以有选择地、动态地开通1024号以上的端口,使得安全性得到进一步地提高。
2、防火墙工作原理
(1)包过滤防火墙
包过滤防火墙一般在路由器上实现,用以过滤用户定义的内容,如IP地址。包过滤防火墙的工作原理是:系统在网络层检查数据包,与应用层无关。这样系统就具有很好的传输性能,可扩展能力强。但是,包过滤防火墙的安全性有一定的缺陷,因为系统对应用层信息无感知,也就是说,防火墙不理解通信的内容,所以可能被黑客所攻破。

图1:包过滤防火墙工作原理图
(2)应用网关防火墙
应用网关防火墙检查所有应用层的信息包,并将检查的内容信息放入决策过程,从而提高网络的安全性。然而,应用网关防火墙是通过打破客户机/服务器模式实现的。每个客户机/服务器通信需要两个连接:一个是从客户端到防火墙,另一个是从防火墙到服务器。另外,每个代理需要一个不同的应用进程,或一个后台运行的服务程序,对每个新的应用必须添加针对此应用的服务程序,否则不能使用该服务。所以,应用网关防火墙具有可伸缩性差的缺点。(图2)

图2:应用网关防火墙工作原理图
(3)状态检测防火墙
状态检测防火墙基本保持了简单包过滤防火墙的优点,性能比较好,同时对应用是透明的,在此基础上,对于安全性有了大幅提升。这种防火墙摒弃了简单包过滤防火墙仅仅考察进出网络的数据包,不关心数据包状态的缺点,在防火墙的核心部分建立状态连接表,维护了连接,将进出网络的数据当成一个个的事件来处理。可以这样说,状态检测包过滤防火墙规范了网络层和传输层行为,而应用代理型防火墙则是规范了特定的应用协议上的行为。(图3)

图3:状态检测防火墙工作原理图
(4)复合型防火墙
复合型防火墙是指综合了状态检测与透明代理的新一代的防火墙,进一步基于ASIC架构,把防病毒、内容过滤整合到防火墙里,其中还包括VPN、IDS功能,多单元融为一体,是一种新突破。常规的防火墙并不能防止隐蔽在网络流量里的攻击,在网络界面对应用层扫描,把防病毒、内容过滤与防火墙结合起来,这体现了网络与信息安全的新思路。它在网络边界实施OSI第七层的内容扫描,实现了实时在网络边缘布署病毒防护、内容过滤等应用层服务措施。(图4)

图4:复合型防火墙工作原理图
3、四类防火墙的对比
包过滤防火墙:包过滤防火墙不检查数据区,包过滤防火墙不建立连接状态表,前后报文无关,应用层控制很弱。
应用网关防火墙:不检查IP、TCP报头,不建立连接状态表,网络层保护比较弱。
状态检测防火墙:不检查数据区,建立连接状态表,前后报文相关,应用层控制很弱。
复合型防火墙:可以检查整个数据包内容,根据需要建立连接状态表,网络层保护强,应用层控制细,会话控制较弱。
4、防火墙术语
网关:在两个设备之间提供转发服务的系统。网关是互联网应用程序在两台主机之间处理流量的防火墙。这个术语是非常常见的。
DMZ非军事化区:为了配置管理方便,内部网中需要向外提供服务的服务器往往放在一个单独的网段,这个网段便是非军事化区。防火墙一般配备三块网卡,在配置时一般分别分别连接内部网,internet和DMZ。
吞吐量:网络中的数据是由一个个数据包组成,防火墙对每个数据包的处理要耗费资源。吞吐量是指在不丢包的情况下单位时间内通过防火墙的数据包数量。这是测量防火墙性能的重要指标。
最大连接数:和吞吐量一样,数字越大越好。但是最大连接数更贴近实际网络情况,网络中大多数连接是指所建立的一个虚拟通道。防火墙对每个连接的处理也好耗费资源,因此最大连接数成为考验防火墙这方面能力的指标。
数据包转发率:是指在所有安全规则配置正确的情况下,防火墙对数据流量的处理速度。
SSL:SSL(Secure Sockets Layer)是由Netscape公司开发的一套Internet数据安全协议,当前版本为3.0。它已被广泛地用于Web浏览器与服务器之间的身份认证和加密数据传输。SSL协议位于TCP/IP协议与各种应用层协议之间,为数据通讯提供安全支持。
网络地址转换:网络地址转换(NAT)是一种将一个IP地址域映射到另一个IP地址域技术,从而为终端主机提供透明路由。NAT包括静态网络地址转换、动态网络地址转换、网络地址及端口转换、动态网络地址及端口转换、端口映射等。NAT常用于私有地址域与公用地址域的转换以解决IP地址匮乏问题。在防火墙上实现NAT后,可以隐藏受保护网络的内部拓扑结构,在一定程度上提高网络的安全性。如果反向NAT提供动态网络地址及端口转换功能,还可以实现负载均衡等功能。
堡垒主机:一种被强化的可以防御进攻的计算机,被暴露于因特网之上,作为进入内部网络的一个检查点,以达到把整个网络的安全问题集中在某个主机上解决,从而省时省力,不用考虑其它主机的安全的目的。
二、市场上常见的硬件防火墙
(1)NetScreen 208 Firewall
NetScreen科技公司推出的NetScreen防火墙产品是一种新型的网络安全硬件产品。NetScreen采用内置的ASIC技术,其安全设备具有低延时、高效的IPSec加密和防火墙功能,可以无缝地部署到任何网络。设备安装和操控也是非常容易,可以通过多种管理界面包括内置的WebUI界面、命令行界面或NetScreen中央管理方案进行管理。NetScreen将所有功能集成于单一硬件产品中,它不仅易于安装和管理,而且能够提供更高可靠性和安全性。由于NetScreen设备没有其它品牌产品对硬盘驱动器所存在的稳定性问题,所以它是对在线时间要求极高的用户的最佳方案。采用NetScreen设备,只需要对防火墙、VPN和流量管理功能进行配置和管理,减省了配置另外的硬件和复杂性操作系统的需要。这个做法缩短了安装和管理的时间,并在防范安全漏洞的工作上,省略设置的步骤。NetScreen-100 Firewall比适合中型企业的网络安全需求。
(2)Cisco Secure PIX 515-E Firewall
Cisco Secure PIX防火墙是Cisco防火墙家族中的专用防火墙设施。Cisco Secure PIX 515-E防火墙系通过端到端安全服务的有机组合,提供了很高的安全性。适合那些仅需要与自己企业网进行双向通信的远程站点,或由企业网在自己的企业防火墙上提供所有的Web服务的情况。Cisco Secure PIX 515-E与普通的CPU密集型专用代理服务器(对应用级的每一个数据包都要进行大量处理)不同,Cisco Secure PIX 515-E防火墙采用非UNIX、安全、实时的内置系统。可提供扩展和重新配置IP网络的特性,同时不会引起IP地址短缺问题。NAT既可利用现有IP地址,也可利用Internet指定号码机构[IANA]预留池[RFC.1918]规定的地址来实现这一特性。Cisco Secure PIX 515-E还可根据需要有选择性地允许地址是否进行转化。CISCO保证NAT将同所有其它的PIX防火墙特性(如多媒体应用支持)共同工作。Cisco Secure PIX 515-E Firewall比适合中小型企业的网络安全需求。
(3)天融信网络卫士NGFW4000-S防火墙
北京天融信公司的网络卫士是我国第一套自主版权的防火墙系统,目前在我国电信、电子、教育、科研等单位广泛使用。它由防火墙和管理器组成。网络卫士NGFW4000-S防火墙是我国首创的核检测防火墙,更加安全更加稳定。网络卫士NGFW4000-S防火墙系统集中了包过滤防火墙、应用代理、网络地址转换(NAT)、用户身份鉴别、虚拟专用网、Web页面保护、用户权限控制、安全审计、攻击检测、流量控制与计费等功能,可以为不同类型的Internet接入网络提供全方位的网络安全服务。网络卫士防火墙系统是中国人自己设计的,因此管理界面完全是中文化的,使管理工作更加方便,网络卫士NGFW4000-S防火墙的管理界面是所有防火墙中最直观的。网络卫士NGFW4000-S防火墙比适合中型企业的网络安全需求。
(4)东软NetEye 4032防火墙
NetEye 4032防火墙是NetEye防火墙系列中的最新版本,该系统在性能,可靠性,管理性等方面大大提高。其基于状态包过滤的流过滤体系结构,保证从数据链路层到应用层的完全高性能过滤,可以进行应用级插件的及时升级,攻击方式的及时响应,实现动态的保障网络安全。NetEye防火墙4032对流过滤引擎进行了优化,进一步提高了性能和稳定性,同时丰富了应用级插件、安全防御插件,并且提升了开发相应插件的速度。网络安全本身是一个动态的,其变化非常迅速,每天都有可能有新的攻击方式产生。安全策略必须能够随着攻击方式的产生而进行动态的调整,这样才能够动态的保护网络的安全。基于状态包过滤的流过滤体系结构,具有动态保护网络安全的特性,使NetEye防火墙能够有效的抵御各种新的攻击,动态保障网络安全。东软NetEye 4032防火墙比适合中小型企业的网络安全需求。
三、防火墙的基本配置
下面我以国内防火墙第一品牌天融信NGFW 4000为例给各位讲解一下在一个典型的网络环境中应该如何来配置防火墙。

图5:网络拓扑结构
NGFW4000有3个标准端口,其中一个接外网(Internet网),一个接内网,一个接DMZ区,在DMZ区中有网络服务器。安装防火墙所要达到的效果是:内网区的电脑可以任意访问外网,可以访问DMZ中指定的网络服务器,Internet网和DMZ的电脑不能访问内网;Internet网可以访问DMZ中的服务器。
1、配置管理端口
天融信网络卫士NGFW4000防火墙是由防火墙和管理器组成的,管理防火墙都是通过网络中的一台电脑来实现的。防火墙默认情况下,3个口都不是管理端口,所以我们先要通过串口把天融信网络卫士NGFW4000防火墙与我们的电脑连接起来,给防火墙指定一个管理端口,以后对防火墙的设置就可以通过远程来实现了。
使用一条串口线把电脑的串口(COM1)与NGFW4000防火墙的console口连接起来,启动电脑的"超级终端",端口选择COM1,通信参数设置为每秒位数9600,数据位8,奇偶校验无,停止位1,数据流控制无。进入超级终端的界面,输入防火墙的密码进入命令行格式。
定义管理口:if eth1 XXX.XXX.XXX.XXX 255.255.255.0
修改管理口的GUI登录权限: fire client add topsec -t gui -a 外网 -i 0.0.0.0-255.255.255.255
2、使用GUI管理软件配置防火墙
安装天融信防火墙GUI管理软件"TOPSEC集中管理器",并建立NGFW4000管理项目,输入防火墙管理端口的IP地址与说明。然后登录进入管理界面。
(1)定义网络区域
Internet(外网):接在eth0上,缺省访问策略为any(即缺省可读、可写),日志选项为空,禁止ping、GUI、telnet。
Intranet(内网):接在eth1上,缺省访问策略为none(不可读、不可写),日志选项为记录用户命令,允许ping、GUI、telnet。
DMZ区:接在eth2上, 缺省访问策略为none(不可读、不可写),日志选项为记录用户命令,禁止ping、GUI、telnet。
(2)定义网络对象
一个网络节点表示某个区域中的一台物理机器。它可以作为访问策略中的源和目的,也可以作为通信策略中的源和目的。网络节点同时可以作为地址映射的地址池使用,表示地址映射的实际机器,详细描述见通信策略。

图6
子网表示一段连续的IP地址。可以作为策略的源或目的,还可以作为NAT的地址池使用。如果子网段中有已经被其他部门使用的IP,为了避免使用三个子网来描述技术部使用的IP地址,可以将这两个被其他部门占用的地址在例外地址中说明。

图7
为了配置访问策略,先定义特殊的节点与子网:
FTP_SERVER:代表FTP服务器,区域=DMZ,IP地址= XXX.XXX.XXX.XXX。
HTTP_SERVER:代表HTTP服务器,区域=DMZ,IP地址= XXX.XXX.XXX.XXX。
MAIL_SERVER:代表邮件服务器,区域=DMZ,IP地址= XXX.XXX.XXX.XXX。
V_SERVER:代表外网访问的虚拟服务器,区域=Internet,IP=防火墙IP地址。
inside:表示内网上的所有机器,区域=Intranet,起始地址=0.0.0.0,结束地址=255.255.255.255。
outside:表示外网上的所有机器,区域=Internet,起始地址=0.0.0.0,结束地址=255.255.255.255。
(3)配置访问策略
在DMZ区域中增加三条访问策略:
A、访问目的=FTP_SERVER,目的端口=TCP 21。源=inside,访问权限=读、写。源=outside,访问权限=读。这条配置表示内网的用户可以读、写FTP服务器上的文件,而外网的用户只能读文件,不能写文件。
B、访问目的=HTTP_SERVER,目的端口=TCP 80。源=inside+outside,访问权限=读、写。这条配置表示内网、外网的用户都可以访问HTTP服务器。
C、访问目的=MAIL_SERVER,目的端口=TCP 25,TCP 110。源=inside+outside,访问权限=读、写。这条配置表示内网、外网的用户都可以访问MAIL服务器。
(4)通信策略
由于内网的机器没有合法的IP地址,它们访问外网需要进行地址转换。当内部机器访问外部机器时,可以将其地址转换为防火墙的地址,也可以转换成某个地址池中的地址。增加一条通信策略,目的=outside,源=inside,方式=NAT,目的端口=所有端口。如果需要转换成某个地址池中的地址,则必须先在Internet中定义一个子网,地址范围就是地址池的范围,然后在通信策略中选择NAT方式,在地址池类型中选择刚才定义的地址池。
服务器也没有合法的IP地址,必须依靠防火墙做地址映射来提供对外服务。增加通信策略。
A、目的=V_SERVER,源=outside,通信方式=MAP,指定协议=TCP,端口映射21->21,目标机器=FTP_SERVER。
B、目的=V_SERVER,源=outside,通信方式=MAP,指定协议=TCP,端口映射80->80,目标机器=HTTP_SERVER。
C、目的=V_SERVER,源=outside,通信方式=MAP,指定协议=TCP,端口映射25->25,目标机器=MAIL_SERVER。
D、目的=V_SERVER,源=outside,通信方式=MAP,指定协议=TCP,端口映射110->110,目标机器=MAIL_SERVER。
(5)特殊端口
在防火墙默认的端口定义中没有我们所要用到的特殊端口,就需要我们手工的添加这些特殊端口了。在防火墙集中管理器中选择"高级管理">"特殊对象">"特殊端口",将弹出特殊端口的定义界面,点"定义新对象",输入特殊端口号与定义区域即可。
(6)其他配置
最后进入"工具"选项,定义防火墙的管理员、权限以及与IDS的联动等。(图8)

图8
四、防火墙对比
在了解了防火墙的工作原理及基本配置之后,下面给大家介绍一下NetScreen 208、Cisco PIX 515E、NGFW 4000-S、NetEye 4032这四款市场上最常见的硬件防火墙在基本性能、操作管理与市场价格上的比较。
防火墙
NetScreen208
CiscoPIX515E
NGFW4000-S
NetEye4032
核心技术
状态检测
状态检测
核检测
状态检测
产品类型
ASIC硬件
硬件设备
硬件设备
硬件设备
工作模式(路由模式、桥模式、混合模式)
路由模式、桥模式
路由模式、桥模式
路由模式、桥模式、
混合模式
路由模式、桥模式
并发连接数
130000
130000
600000
300000
网络吞吐量
550M
170M
100M
200M
最大支持网络接口
8个
6个
12个
8个
操作系统
ScreenOS
专用操作系统
专用操作系统
专用操作系统
管理方式
串口、CLI、Telnet、Web、GUI
串口、Telnet、Web、GUI
串口、Telnet、Web、GUI
串口、Telnet、GUI
市场报价
142,000RMB
80,000RMB
138,000RMB
148,000RMB
AMD adds 32-, 64-bit embedded processors
Feb. 12, 2007
AMD has introduced several new versions of its Geode LX processor, and has added a "low power" version of its 35-Watt dual-core Athlon 64 X2 to its embedded roadmap. Additionally, the company is offering three new reference designs, including an ATCA blade, a SOHO NAS server, and an "ultra-value client."
AMD‘s slew of embedded processor news announcements were timed to coincide with the opening of the Embedded World Exhibition & Conference in Germany on Feb. 12.
New Geode LX models
AMD has added two new models to itsGeode LX SoC (system-on-chip) family, which previously consisted only of the 500MHz LX800@0.9 part. The new Geode LX900@1.5 model runs at a slightly higher voltage -- and consumes a little more power -- while the LX700 runs slightly cooler.
CPU Clock Typical Power TDP
LX700 433MHz 1.3W 3.1W
LX800 500MHz 1.8W 3.6W
LX900 600MHz 2.6W 5.1W
AMD‘s Geode LX line

Geode LX function
block diagram
(Click to enlarge)
The Geode LX was the first and only embedded processor designed by AMD after itacquired the Geode line from National Semiconductor in 2003. Fabbed on a 0.13-micron process, the chip has an x86/x87 compatible core, and integrates typical northbridge functions such as memory and graphics controllers. It is designed for use with AMD‘s CSCS5536 companion chip.
New RDKs
Also new from AMD are a pair of "reference design kits" (RDKs) based on its Geode LX SoC line, and one new reference design based on dual Opteron processors. The designs include: SOHO NAS (network attached storage for small office, home offices) -- A Linux-based hardware/software reference design said to support the sharing of home movies, music, and other forms of data while providing redundancy, back-up, and security features. The design‘s hardware features include gigabit Ethernet, board-level SATA, a 4-drive bay storage system option, and an integrated memory controller. According to Jeff Chu, AMD‘s division manager for embedded, "It‘s good at handling data movement -- in the range of 10-15Mbps throughput. That‘s above some of the RISC-based designs that are out there." Chu also noted that a third-party customer offers a BSD stack for the design.
Geode LX UVC (ultra-value client) -- Described as a fifth-generation RDK for designers of low-cost PCs, SBCs (single-board computers), POS (point-of-sales/services) devices, corporate thin clients, network appliances, and kiosks, the RDK includes an optical drive and a hard drive. It supports Linux, Windows CE, or Windows XP, Chu said.
ATCA blade reference design -- Designed in partnership with Pinnacle Data Systems (PDS), the design supports Dual "2P" Opteron processors, using a Broadcom chipset. As for OS support, Chu said, "We always work with MontaVista and Wind River on Carrier Grade Linux stuff, and lately we‘ve been working with FSMLabs on real-time Linux support as well. We‘re committed to the open platform approach, and are enabling our customers to make the choices they need to make."
Early RDK customers reportedly include Advansus, Advantech, ICP, and Liteon.
Embedded roadmap additions
Finally, AMD has announced the addition of two semi-existing processor designs to its AMD64 Longevity Program, which guarantees at least five years of production availability. Both fit AMD‘s relatively new AM2 motherboard socket, and thus support DDR2 memory. And, for telecom applications such as ATCA and MicroATCA boards, both support ECC (error checking and correction) memory, Chu said.
One is the 3400+ model in AMD‘s line of "low power, small form factor" dual-core Athlon 64 X2 processors. With a TDP (thermal design power) of only 35 Watts, this part runs considerably cooler than the standard 85 Watt and "low power" 65 Watt parts in AMD‘s normal Athlon 64 X2 line. Additionally, Chu notes that the chip has a 20 Watt low-power state, and can be configured via BIOS settings to stay within that envelope.
The Athlon 64 X2 3400+ is "semi-new" because in the past, AMD appears to have marketed the chip with a slightly faster clock rating as the 64 X2 Dual-Core 3800+ (ADD3800IAT5CU for OEMs, and ADD3800CUBOX for retail). Although "shipping" for nearly a year, short supplies have resulted in street prices upwards of $400 for the retail box version. Thus, AMD appears to have settled for a slower clock speed, and added the part to its Longevity Program to reassure customers of its commitment to the part.
The other chip newly added to the AMD64 Longevity Program is the Sempron 3000+ (SDD3000CNBOX), a relatively inexpensive single-core part that also has a TDP of 35 Watts.
Availability
The Geode LX900 and LX700 appear to be available now. The three RDKs have all shipped to customers, according to AMD. The Athlon 64 X2 3400+ is said to be available, although as of publication time, it had not yet been added to AMD‘s processor feature comparison chart. The Sempron 3000+ is shipping now.
Earlier this month,AMD added its dual-core Turion 64 X2 Model TL-52 and single-core Mobile AMD Sempron 3500+ to the AMD64 Longevity Program. Meanwhile, competitor Intel is rumored to be prepping aPentium M-based SoC that could compete with Geode processors.
Related Stories:AMD aims Geode LX at "x86 everywhere"
Intel prepping Pentium M-based SoC?
Geode finds a new home at AMD
Single-chip x86-compatible chipset runs Linux
AMD offers free Geode-based EPIC SBC design
Mobile 64-bit chips arrive on AMD‘s embedded roadmap
Intel, AMD drop out of mobile handset chipset game
(Click here for further information)
Server
zhz02 server
Server对象
sql server
Linux Home Server HOWTO - MySQL Server
SQL Server日期计算
Sql Server 整理收集
Community Server专题
Sql Server 常用函数
SQL SERVER实用技巧
全面解析Server对象
Reverse Proxy Server
SQL Server日期计算
mail server info
SQL Server基本函数
Linux LPD Print Server
Apache Server 的個案討論
SSH2 Server 架設
Apache Http Server 使用
Server Push详解
built the WebDAV server
About Secure Server IDs
AJAX Server 入门实例
The DINAMelt Server